Introduction
At the present time, network planning and design play an essential role, as it is the foundation for effective network monitoring. In order to ensure a high level of service quality maintenance, it is important to have a deep understanding in terms of the way network components fit together. Most frequently, specialist network designers, IT administrators, and engineers take responsibility for the proper implementation of network infrastructure. In fact, these individuals are required to ensure that the company’s network infrastructure design includes a clear map of the network and details of the network security architecture. As a result, the organization would be able to strengthen business connections and offer the highest quality service to both existing and potential clients.
When it comes to ElekTron, this company is widely known as a supplier that takes appropriate measures to build electronic components for numerous private and government customers. Currently, its networking infrastructure is outdated, which is why it has been attacked by hackers lately. Furthermore, taking into consideration that networking equipment does not meet computing throughput requirements, the new network design should address this problem in the first place. In case this point is ignored, there is a high likelihood that ElekTron will face performance and security issues. Therefore, the proposed networking design takes into account the main disadvantages of the previous networking infrastructure and suggests effective improvements. For instance, the implementation of innovative design is based on a reconfiguration of the organization’s network hardware, elimination of performance bottlenecks, and ensuring the quality of service. Consequently, ElekTron’s activity is predicted to result in reduced costs, improved performance, better business continuity, customized solutions, and enhanced network security.
Network Design Proposal
Proposed Network Design
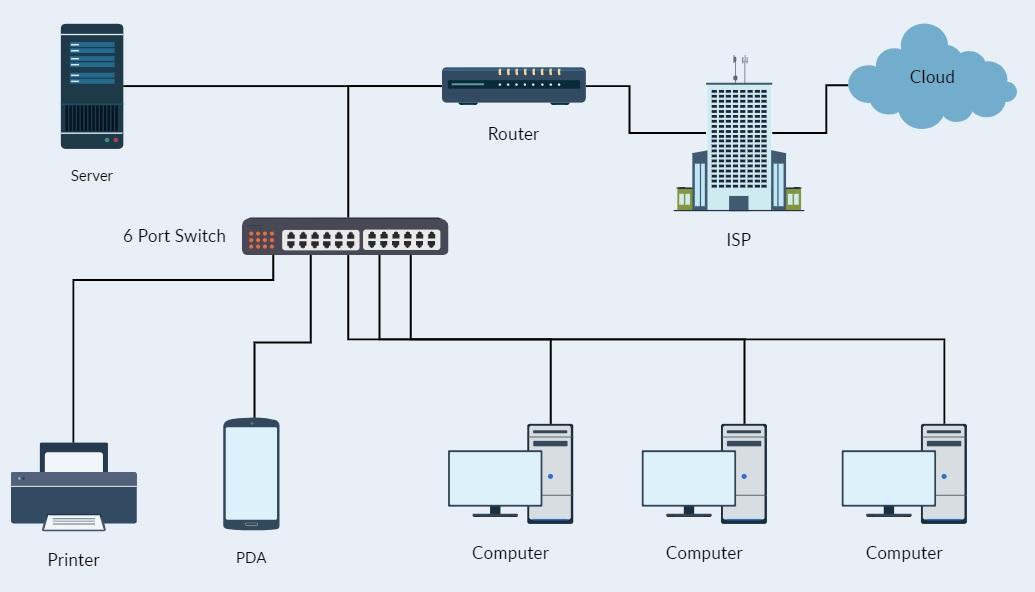
The organizational network topology below considers various design principles to enhance the achievement of a secure system. For instance, in order to minimize the exposure of the systems to external and internal attacks, defense-in-depth principles are taken into consideration by ElekTron. In fact, this principle is based on the combination of high-quality in-depth defense mechanisms that are installed with the help of firewalls in different locations. Accordingly, the company has the opportunity to use robust security measures. Moreover, the implementation of a wireless access point is an approach to achieving a secure network through minimized access to physical workstations by malicious visitors. Another principle under application by the topology entails the compartmentalization of information. The design accomplishes this by creating zones whose access is under the control of a firewall.
Secure Hardware Components
The security of the systems relies on the combination of reliable hardware components in the network infrastructure. Thus, to achieve the security needs of the merged organization, the topology below intentionally integrates various elements in it to deliver secure systems in support of service delivery. One way the design meets the needs of ElekTron involves centralizing the databases and separating them for different purposes. Installation of commercial, web and email databases in the organizational headquarters provides a means through which system administrators can enhance monitoring of data access to safeguard its integrity. Another secure hardware component integrated into the design is firewalls and routers. The integration of firewalls at the entry of LAN and the server access points provides several security layers hard to break in an attempt of illegal entry into the system, thus maintaining a secure network.
Communication Channels
The network topology for ElekTron provides various mechanisms to facilitate different types of communication through the establishment of secure channels. The adoption of a star topology achieves a dedicated connection for point-to-point transmissions with other components. In order to accomplish network security, the mix of directed and undirected communication channels should be taken into account. The directed or wired communication channel utilizes on duplex twisted pair cable to establish a point-to-point connection between the various nodes within the network. Any compromise of a specific channel does not affect the availability of other nodes, thus facilitating the achievement of a reliable system.
A Virtual Private Network (VPN) Tunnel should be implemented from the firewall of ElekTron. This intervention will allow the user to communicate and access data between the two sites without opening the PC’s to the public internet. Instead, when they connect to the VPN, the remote desktop (RD) client acts as if it is part of the same network and accesses the information that is desired securely. A demilitarized zone (DMZ) has been implemented in the network diagram as well. The DMZ will act as a buffer between the internet and the internal network. The DMZ is placed behind the firewall. This is done so that the DMZ can take advantage of the blocking protection that is provided by the firewall. The DMZ is essentially in place to lessen the impact of a compromise to the system via the public access systems.
Wireless communication channel achieves security through the prevention of damages from unauthorized access to computers and data. As a result, the nodes and hosts achieve significant uptime, thus ensuring the availability of services and resources to users because it does not rely on another host or shared channel to communicate. Subsequently, the LAN maintains secure communication by eliminating the risk of intrusion through notifications from installed attack detection software.
Regulatory Compliance Requirements
The proposed network topography seeks to adhere to the organization’s regulatory compliance requirements of enhanced security and budget in various ways. For instance, the topology involves a light and straightforward design, which makes it possible for IT administrators to detect and handle a threat (Lotfi et al., 2021). Notably, the decision to develop a topology with minimal devices through sharing of several resources such as a database and printer seeks to adhere to the budget provisions of thousands of dollars thus making it a viable design for implementation.
Integration Problems
The process of implementing the proposed network (see Appendix A) has several potential security threats and challenges, which require the use of appropriate management approaches. The implementation process involves a risk concerning data loss through deletion or damage. Therefore, the process should include a system backup for recovery in case data gets lost or damaged during the integration process. Another threat entails inconsistent device configuration and physical damage. The establishment of a work schedule and use of manufacturer’s manuals can assist in ensuring proper system configuration to seal possible entry routes. The use of manufacturer’s manuals would also help in identifying the appropriate way of handling various devices during installations to avoid physical damage, which would introduce weak points to the system.
The introduction of viruses and worms to the network is a risk involved in the integration. Therefore, to ensure no introduction of infectious applications into the system takes place, the team should adequately scan all the data before integrating the systems. Taking into consideration that the is strongly associated with hacking, it is tremendously essential to install intrusion and detection software. It is expected that this measure can be beneficial in the context of monitoring the LAN for any abnormalities. The hardware and software should also be reviewed from different perspectives with the purpose of validating their integrity. Budget overruns are another threat to the implementation of the network topology as the project should fall under the provided budget lines. In other words, to avoid exceeding the budget allocations, the team should purchase devices by reviewing costs to avoid over expenditure.
Project Justification
The table mentioned above demonstrates that there is an opportunity to achieve a secure network in case robust resource access control measures are considered the priority. In this way, the company also has the opportunity to reduce costs. Databases and servers are expensive to purchase; therefore, their retention results in a reduction of budget strain that would emanate from the need to replace the existing one with one.
The topology suggests the addition of various components into the resulting network to further support the needs of ElekTron. These include several switches, a printer, databases, wireless access points, and firewalls. In fact, the purchase of the additional equipment will involve large budgetary allocations in exchange for improved service quality and system security. The addition of more firewalls in the network provides an extra security layer purposed to achieve robust access control of system services and resources. The installation of a printer in the organization will avoid outsourcing printing services from elsewhere, which may potentially disclose sensitive information to unauthorized users depending on the information classification level. Centralizing the database intends to achieve data security by minimizing the exposure surface as well as by delivering increased attention from administrators.
Notably, the topology achieves physical separation of data by installing several databases. The physical separation of databases seeks to reduce the risk of losing or compromising the integrity, confidentiality, and availability of sensitive information like in the case of single storage. In order to maintain a high level of security in the company, it is essential to take into account the process of installing wireless access points. In fact, this measure is expected to limit access to workstations, thereby resulting in a considerable decrease in the number of cases related to physical damage to the equipment. In case this recommendation is ignored, there is a high likelihood of facing security concerns related to data availability.
Project Deliverables
Currently, ElekTron experiences a variety of issues affecting the quality of its products and services, although problems related to communication and information flow play the main role in terms of security threats. For example, it is essential to note that the human resource structure places the director of the IT department as the person taking full responsibility for issues that affect the company. As a result, other employees are required to report to the director of IT department (Govindan et al., 2017). As a result, there is a lack of collaboration within the department, which in turn affects the efforts towards securing the LAN. The help desk and PC technician need to report to the network administrator who after establishing the magnitude of issues raised should raise the concern with the director accordingly.
In other words, the breakdown of the information flow consumes time, especially when the director needs to involve network administrators on issues arising from PC technicians or help desk. At the same time, the use of the suggested network design is expected to result in reduced costs, improved performance, better business continuity, customized solutions, and enhanced network security. Accordingly, taking into consideration that the proposed network design is likely to contribute to a consistently high level of the overall performance in ElekTron, it should be implemented in the near future. When it comes to installation, it is essential to connect hardware and installation labor.
Project Plan & Timeline
Elektron’s network architecture and design present significant system security concerns. Simultaneously, the implementation of a single firewall to control access to system resources proves inadequate to support network security. Technically, the network requires the installation of several firewalls to provide adequate protection to the system. For example, the absence of a firewall between the Internet and the router undermines network security, as there is a lack of monitoring of external requests (Albert et al., 2020). Consequently, this exposes the network to attacks as a result of a compromised router. Furthermore, the servers need proper protection through the installation of multiple security layers to control access and requests from various workstations.
In order to implement the proposed network successfully, it is essential to follow several crucial steps. Firstly, the process of verification of the business goals and technical requirements should be considered. Secondly, it is important to pay attention to the determination of the features and functions required to meet identified needs. In addition, Elektron’s representatives should perform a network-readiness assessment, as well as create a solution and site acceptance test plan. Finally, a comprehensive project plan can be created with the purpose of improving the overall organizational performance.
When it comes to the timeline related to the implementation of network design, it is presented in the table below:
Conclusion
A secure network acts as the backbone of an organization, especially those that operate in different geographical locations. Exposing systems to attacks, a company undergoes a lot of attacks that could easily hurt its operations, rendering it insolvent. Indeed, the merging of companies presents numerous challenges that may result in a fall of an organization. Therefore, the process requires great caution to ensure the alignment of all system components to the business process and regulations. Proper system configuration, installation of firewalls, intrusion detection software, and system backup achieve robust measures that ensure the achievement of a secure system fit for business operations.
References
Albert, H., Purcell, R., Wang, Y., Kao, K., Mareka, M., & Katz, Z. et al. (2020). Designing an optimized diagnostic network to improve access to TB diagnosis and treatment in Lesotho. Plos One, 15(6), 23-26. Web.
Govindan, K., Fattahi, M., & Keyvanshokooh, E. (2017). Supply chain network design under uncertainty: A comprehensive review and future research directions. European Journal of Operational Research, 263(1), 108-141. Web.
Lotfi, R., Mehrjerdi, Y., Pishvaee, M., Sadeghieh, A., & Weber, G. (2021). A robust optimization model for sustainable and resilient closed-loop supply chain network design considering conditional value at risk. Numerical Algebra, Control & Optimization, 11(2), 221. Web.
Appendix A
Networking Design