Introduction
Companies are trying to develop competitive advantages to become leaders or remain in the market. Information security management (ISM) is one of the areas that can help businesses achieve this goal. Such aspects as contingency planning, security awareness and policies, risk management, and assessment, as well as security staffing, should gain maximum attention as they contribute to the improved performance. This paper includes a description of the information security management program developed for Pronto Courier.
Reason for RFP
Pronto Courier is a small courier company located in Abu Dhabi. The organization has clients and partners throughout the UAE. Pronto Courier is growing steadily. There are plans to open an office in Dubai, which will enhance productivity and will lead to the customers’ satisfaction. A new information system will be implemented. The company has had a number of issues with delivery details, which led to customers’ dissatisfaction and even some fines. The new system is designed to address those aspects. However, there are concerns that the company may have issues associated with information system management.
Furthermore, the company has to operate in a highly competitive environment. The ability to manage information properly is a competitive advantage any successful organization should have. Finally, the overall performance of employees, as well as their communication, has deteriorated, which can be a result of improper information system management.
Outline of Pronto
Some of the most important functional areas to be taken into account are as follows: customer service, logistics, and human resources. It is necessary to consider major information assets related to each of the mentioned functions. Pronto Courier has a database of its customers, which includes such details as contact details, addresses, delivery data, and some financial data. As for the logistics, such assets as routes, information on partners, and the company’s own vehicles and warehouses should be properly managed and protected. Information assets related to human resources include personal data of employees as well as data on their salaries and their financial details.
When developing a sound ISM program, it is essential to consider internal and external interdependencies existing in the organization. The internal interdependencies involve a close collaboration between customer service and logistics operations. Thus, customer service professionals help customers to place orders and learn about the delivery (terms, location, phase, and so on). Clearly, customer service professionals need some information related to the logistics department. Both departments refer to similar areas of the company’s information system. At that, the logistics department can fail to update the databases timely, which has led to some issues mentioned above.
As for external dependencies, Pronto relies on a company providing cloud services to store its data. The company does not have enough resources to ensure data storage within the organization’s facilities. The company does not plan to use another approach with a new IS, so it is important to take this into account. Security issues associated with this method are quite burning. The growth of the database also poses some threats as it can lead to the system failure and disclosure or distortion of some data.
The approximate number of employees is 50, including customer service professionals, logistics professionals, accounting, HR professionals, top management, and drivers.
Contingency Planning
Business Impact Analysis
Contingency planning involves four major components: business impact analysis (BIA), incident response plan, disaster recovery plan, and business continuity plan. The business impact analysis provides an assessment of the impact of an organization during a disruption (Mcilwee, 2013). The analysis should include such key elements as the identification of the functional area, the time before the impact, the rating, recovery time, priority ranking, organizations that will need the functional area, organizations that will be needed, safe options. The template to be used is a modified variant of the BIA form by Okolita (2009). The author includes the ratings and recovery time as well as the safe zone, which provides an important quantitative assessment. However, it is important to add some details concerning possible stakeholders, and, hence, organizations that will need the unit or will be needed (see table 1).
Table 1. BIA Template.
- FA – Functional Area (name);
- FN – Functional Name (name);
- PR – Priority Ranking (5 – crucial, 4 – very important, 3 – important, 2 – neutral, 1 – not important, 0 – irrelevant);
- TBI – Time Before Impact (0 – two weeks or more, 1 – one week, 5 – one to three days, 10 – one day, 20 – four hours, 40 – immediate);
- CI – Customer Impact (5 – high, 3 – medium, 1 – low, 0 – none);
- FI – Financial Impact (5 => 100K, 4 =>50K, 3 =>20K, 2 =>10K, 1 =>5K, 0 – none);
- II – Image Impact (5 – high, 3 – medium, 1 – low, 0 – none);
- RT – Rating Total (The sum of PR, TBI, CI, FI, II);
- R Time – Recovery Time (AAA – immediate recovery, AA – recovery within one to four hours, A – the same day recovery, B – recovery within one to three days, C – recovery within one week, D – recovery within two or more weeks);
- ONFN – Organizations that Need the Functional Area (name);
- ON – Organizations Needed (name);
- SO – Safe Options (name).
This template includes all the necessary data that will help managers to assess the impact of any situation. It involves the analysis of quantitative and qualitative data. When considering the table, the manager will be able to make a quick decision on the steps to undertake and resources to allocate in each case.
Incident Response Plan
The incident response plan is a description of the procedures and processes that “anticipate, detect, and mitigate the effects of an unexpected event that might compromise information resources and assets” (Whitman, Mattord & Green, 2013, p. 138). The template should include a number of critical components. Beaver (2013) provides an efficient template for the incident response plan. It can be presented in the form of a checklist with minor modifications (see table 2).
Table 2. Incident Response Plan.
This template is a detailed plan that can be applied to many organizations. It addresses all the aspects associated with responding to an incident. It is noteworthy that it includes such important elements as learning lessons and training as well as revision. Thus, the template forces employees to learn the lesson by documenting it and training to react accordingly. In many cases, a successful response to an incident makes people feel safe and forget about past experiences. More so, changes occur all the time. For a company that is undergoing substantial changes, it is vital to keep all records concerning incidents up-to-date. Constant updates will make the procedures very effective.
Disaster Recovery Plan
The disaster recovery plan usually includes steps to be undertaken and the time necessary to implement each step. An effective recovery plan will include such sections as recovery strategy summary, recovery tasks, recovery personnel, critical resources recovery timeline, and critical partners (The building blocks for a successful recovery program, 2014). This template is appropriate as it includes all primary elements that can help the company to recover from the incident.
First component
The first component of the plan includes the description of possible incidents and strategies to be used as well as recovery tasks, resources needed, critical partners, and recovery personnel (see table 3). Importantly, the recovery strategy section includes a list of major strategies that will be used in each incident. The recovery tasks section includes a description of the particular steps and processes necessary to implement the strategy. For instance, if the strategy is to “relocate to an alternative work location,” the recovery tasks will include identification of the equipment needed, the provision of the necessary equipment, and so on (The building blocks for a successful recovery program, 2014, p. 2). It is also beneficial to note an employee or a team responsible for this or that task.
Table 3. First Component.
Recovery timeline
The recovery timeline is an important element as it allows employees to keep track of the incident and make sure that the company undertakes the necessary steps in a timely manner (see table 4). The template provided below is a modification of the timeline that can be applied in many organizations (The building blocks for a successful recovery program, 2014, p. 2).
Table 4. Recovery timeline.
It is necessary to note that the timeline is quite approximate, but it is beneficial to achieve a similar result and bring everything to be normal within 30 hours. This will ensure operations continuity and effective recovery. Clearly, the time required to bring the operations back to normal depends on the complexity of recovery tasks and the seriousness of the incident.
Business continuity plan
Business continuity planning (BCP) is an essential part of risk management as well as information system management. BCP involves the development of a sound strategy ensuring the protection of the organization’s assets and the ability to function properly in case of a disaster (Whitman et al., 2013). The template used in this paper includes all the central segments of an efficient BCP (Business continuity plan, n.d.). Still, there are some minor modifications based on a template developed to meet the needs of small companies (Business continuity management, n.d.).
Basic data
It is crucial to make sure that the date of the most recent revision is noted (see table 5).
Table 5. Basic data.
Distribution list
Two copies of the document can be provided to some employees as they may need a copy at their home (see table 6).
Table 6. Distribution list.
Program administration
It is important to provide the scope of the BCP and its primary objectives to ensure that the plan is precise and addresses particular issues (see table 7).
Table 7. Program administration.
Business continuity organization
It is important to include a chart of the team focusing on business continuity procedures (see fig. 1).
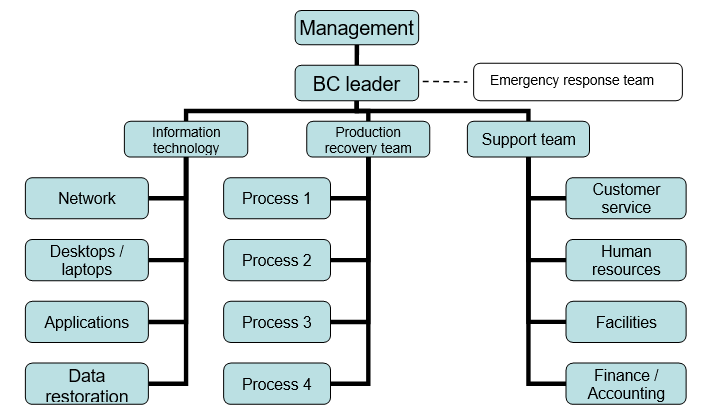
This section also provides contact details of the team members who have to be in touch in case of an emergency (see table 8).
Table 8. BC team contact details.
The analysis of business and BC procedures
This component includes the business impact evaluation as well as a recovery plan. These are provided above in Business Impact Analysis, Incident Response Plan and Disaster Recovery Plan. These sections include all the necessary information on the analysis of the impact as well as a detailed description of the procedures to be implemented.
Training and testing
This section contains the curriculum for the BC team members’ training. Samples of exercises, workshops and topics for discussion should be included. Furthermore, this component also includes the description of testing procedures, their timelines and sample tasks.
Program maintenance
This component focuses on the program’s constant revision and improvement. It includes schedules and triggers for the review of the BCP. It should involve assignments for regular reviews of the plan. Some information on corrective measures should be provided.
Enterprise Information Security Policy
Purpose Statement
This ISP establishes the central information security procedures for Pronto Courier devices and resources as well as communication. The policy is aimed at setting a direction for the company’s security procedures ensuring confidentiality, availability of information within the organization and integrity.
Scope
The Pronto Courier applies to all people who use technology resources of the company including (but not limited to) employees of the company, customers, retirees, partners. Importantly, remote access to the company’s information is similar to the direct access.
Exclusions
A person can be exempted from this ISP upon the written approval of Operations Manager only.
Definitions
Definitions are available through the IT Key Definitions provided in the company’s Policy.
Policy
Information security (IS) is referred to as the protection of data including hardware and software that transmit, process and store information. The IT Officer of Pronto Courier is responsible for designing and implementation of the ISP. This ISP is based on the ISO 27001. The IT Officer is responsible for providing annual reports on the functioning of the IS and the implementation of the ISP.
Information assets are vital for the proper performance of the organization. It is possible to identify the following threats to IS: malicious action, employee error, system failure, damage caused by imprudence, negligence and natural disaster. In particular, any of these threats can lead to the damage or (complete or partial) loss of data, resources damage, and compromised confidentiality. The IT department is responsible for reducing the risks, preventing any possible errors and malfunctions, as well as developing proper measures to mitigate the outcomes of any undesirable disruption of the system.
The company’s technology prevents and tracks hazardous access (if any) to the data. When the unintentional detrimental access is traced, the system recommends preventing future instances of such access. When intentional detrimental access is traced, the system regards it as malicious, and the further access can be prohibited. After an investigation, the access is provided with recommendations concerning prevention of such detrimental access. In some cases, such measures as fines or even legal prosecution can be undertaken. In this case, the IT and legal professionals collaborate to implement the most comprehensive investigation and corrective measures.
Pronto Courier reserves the right to store, view and transmit any information that goes through its information system. The information within the access option can be reviewed and used without the permission of the company. To access any additional information or obtain another access option, the user has to ask for a written permission granted by the IT manager and the corresponding department’s head. The company also reserves the right to use the data for research and marketing purposes. The data can be provided to third parties but confidentiality of users is guaranteed. Confidential information (financial data, personal data, some contact data) will not be given unless there is the inquiry of authority.
Associated Regulations / Policies
- ISO 27001
- Pronto Courier Confidentiality Policy
Associated Procedures
Associated Forms
- The ISS Functioning Report.
- Malfunctions / Malicious Activities Investigation Report.
- Notification of the Update.
- Inquiry of the Access.
- Malfunctions / Malicious Activities Detection Report.
Review Schedule
This policy is reviewed each February by the IT manager and the company’s CEO.
Issue Specific Security Policies
The List of Major ISSPs
- Fair and Responsible Use of the Company’s Database;
- Detecting and Reporting Malfunctions and Malicious Activities;
- Fair and Responsible Use of Office E-mail;
- Sharing Data Through the Company’s Network;
- Access Control;
- Physical Security;
- Information Security Awareness;
- Prevention of Transmitting Viruses;
- Security Accreditation and Certification;
- Personnel Screening.
Fair and Responsible Use of Office E-mail
Statement of Policy
This policy focuses on the fair and responsible use of office e-mail. It is intended for the company’s employees who are expected to comply with the content of this policy. Email is regarded as an official method of written communication among the company’s employees. It is expected that all emails are processed (read and responded) in a timely manner. Each employee is provided with an email as well as the list of contacts (email addresses) of all the employees of the company.
Appropriate Use
Employees are to use the devices provided to use the company’s email. However, laptop users are also permitted. To ensure proper privacy protection, laptop users will have to obtain written approval of the IT manager. The wireless transmissions will be protected through encryption. In some cases (emergency), remote work is possible, but the transmission will be secured through the accepted firewall solution. It is strictly prohibited to use non-standard hardware and software.
Systems Management
The IT Manager is responsible for the proper configuration of the Access points in accordance with the System-Specific Policy. All the users of laptops (if any) are responsible for ensuring that their devices are configured properly. All the employees must not change any configurations.
Violations of Policy
The company reserves the right to undertake any measures accepted for the violation. These steps may include legal actions and employment termination. Written notification with the recommendation to avoid further actions or similar actions in the future in case of minor as well as first violations is the most common measure. Investigation and the measures such as employment termination, fines or legal action are steps undertaken in case of repetitive or major violations. Both minor and major violations are reported as defined in the Information Security Policy. All the instances of violations are also recorded.
Policy Review and Modifications
This policy is reviewed annually by the IT manager and the company’s CEO. Changes are included if necessary, and all the employees receive the corresponding notification.
Limitations of Liability
The company does not admit any liability for any violation of this policy or any local, state or federal law or regulation. Any person who has violated any regulation or law will not be protected or assisted.
Information Security Awareness Program
Information security awareness program is an important element of the ISM of any organization. Winkler and Manke (2013) outline key characteristics of a successful program. First, it should have a support of the upper management of the company as it will ensure the availability of the necessary resources. Therefore, it is important to provide a presentation (for example, a newsletter) to the top management where the benefits of the program are revealed.
Furthermore, it is vital to engage some or even all the departments, which will ensure active participation of employees as well as the incorporation of the program into the culture and common practices of the company. Winkler and Manke (2013) also stress that it is vital to train employees how to do things safely rather than telling them what they cannot do. Another important feature of an effective program is creativity as creative programs attract employees and makes them engaged.
The timeline is crucial, and 90-day programs are the most effective. It is necessary to focus on three topics during these programs to makes sure that each topic is discussed properly and reevaluated regularly. Finally, each program should rely on a set of materials that include posters, newsletters, blogs, simulations and so on. It is possible to consider examples of three types of materials: posters, newsletter and a training calendar.
Security Awareness Posters
The posters provided below can be regarded as illustrations of major features of a successful security awareness program.

One of the posters dwells upon the use of passwords, which is one of the most important issues related to information security (see figure 1). It is creative and appealing as it contains understandable messages and metaphors. People are hooked with the picture of a child and the catching parallel with a “sticky mess” (Passwords are like bubblegum, n.d.). Another poster addresses the issues concerning encryption (see fig.2).

This poster is likely to appeal to the vast majority of people as they know who is depicted. Many people are fans of the famous saga and will definitely memorize the picture as well as the message. Clearly, it Is not enough to have posters as comprehensive training is crucial.
Training Calendar
As has been mentioned, an effective training course should focus on a number of interrelated topics and reevaluate them regularly. The training course will focus on the use of the company’s email and the use of passwords. It is possible to consider a one-month course as an example. The training sessions will be held weekly.
Security Awareness Information Newsletter: Using Corporate Email Responsibly and Effectively
The newsletter provided below is a modified variant of the document developed for an international company (OUCH, 2014).
Using Corporate Email Responsibly and Effectively
- Topic: Using Corporate Email Responsibly and Effectively
- Contents: Autocomplete:
- CC/BCC;
- Emotion;
- Privacy;
- Password;
- Resources.
- Contact: [email protected].
Overview
Email has already become an indispensable part of daily as well as professional life. It seems that everyone knows how to use it properly as it is as simple as can be. Nonetheless, there can be various pitfalls when it comes to the usage of the corporate email. This newsletter provides some tips that will allow employees to avoid making any mistakes and be an effective user.
Autocomplete
Autocomplete is a useful feature that helps save time that is often scarce. When you start typing the email address of a person, it automatically appears, and you do not have to waste time typing it in full. However, there are some hazards associated with this helpful option.
It is common to have several addresses that are similar. Thus, being in a hurry or less attentive due to the workload, you may send the email to a wrong person, which can result in various issues including but not confined to security policy violation, confidential information disclosure and so on. Such events may lead to fines or even termination of employment for the employee and the loss of competitive advantage or even revenue as well as disruption of the reputation of a company. To avoid such risks, you should always double check the addresses as well as names before you click ‘send.’
CC / BCC
Email clients have CC and BCC options. CC means ‘carbon copy’ that enables you to send the email to keep people (other than those you mentioned in the ‘To’ section) informed. BCC stands for ‘blind carbon copy,’ which keeps people informed but no one (except the people mentioned in the BCC section) knows that they have received the email. These options are often associated with some issues when it comes to replying.
Thus, when you reply an email with CC section, you should consider sending the email to all of them or only some (or none) of them. When sending sensitive emails, it is better to reply to the sender of the email. Make sure you do not use ‘Reply All option’, in this case. When sending a letter with BCC option, you should make sure that people from the BCC list will not use “Reply All’ option. In case they do, everyone will see that you used the option, which may and will affects the relationships with colleagues. Therefore, make sure that you send emails to people you really want to share some information with. Think of the reply options for them as well.
Emotion
Never send emails when you are emotionally charged. Even if you delete it from the list of your sent emails, it will still remain the system. Such emails may often disrupt friendly relationships and create a tense atmosphere in the workplace. If you feel you are too emotional, you can write a message in any type of document (for example, Microsoft Word) and have a short break. Drink a cup of coffee, or you can even call a person to resolve the issue. Only when you feel more relaxed, you can write an email (if necessary). This will help you avoid conflicts and tension in the working place.
Privacy
Privacy is one of the major concerns related to email. You should remember that your email can appear anywhere once you sent it. It can be forwarded or placed in some forums or blogs. Therefore, you should carefully choose the data as well as addresses. In case you need to share some important and confidential information, you should choose the face-to-face or telephone communication. Of course, you should remember that using corporate email should be responsible and fair. You should not use it to send private messages. Clearly, mind your language and files or links you send. Remember that the employer reserves the right to monitor your email.
Password
The password is one of the ways to keep your email safe. You should make sure that no one knows your email password. Even if you decide to share it (in case you have no Internet access but need to use your email), you should change the password. Of course, many employees use one password for all the systems. This is quite ineffective and hazardous as someone may access your email account or other systems, which can be used against you personally or the company. Finally, you should choose a sound password. Using the name of the dog or a favorite color is quite irresponsible. Make sure your account is protected to avoid any misunderstanding.
Resources
Ouch. (2014). Web.
Risk Assessment
Risk assessment is one of the most important elements of risk management. It enables to identify and evaluate as well as prioritize risks, which, in its turn, allows the manager to develop strategies to avoid the risk or mitigate its consequences. It is also important for proper allocation of funds within the organization. It is crucial to pay specific attention to the most vulnerable system or the most common risks. Like any other organization, Pronto Courier needs to address the risks in many spheres. Pronto Courier is the company providing delivery services including hazardous materials delivery. One of the forms that can help assess risks will be general risk assessment form (see table 9). It is quite general, but it helps to evaluate the most common risks quite easily.
Table 9. General Risk Assessment.
This template is detailed and easy-to-use. Notably, the evaluation of the risk before and after the corrective measures is included. This enables the manager to assess the effectiveness of measures employed and develop more efficient strategies if necessary. The template also includes such elements as people affected and resources needed, which helps the manager remain focused and collect all the necessary data that can be used when creating departments’ or the organizations’ budget.
Another important sphere is the provision of hazardous materials delivery service. The risk assessment includes the analysis of additional data (see table 10). Such elements as emergency procedures and first aid are critical. The description of the material’s properties should be quite detailed and include the features of materials when transported, carried, exposed to particular temperatures.
Table 10. Hazardous Materials Risk Assessment.
Another important aspect to consider is the risk associated with lone working. The template includes all the necessary details to assess risks associated (see table 11). Clearly, this form is mainly related to the work of drivers who may be exposed to such risks as robbery, terroristic attack, natural disaster, and so on. It is necessary to note that in this template, the hazards are categorized, which makes the assessment more convenient. It is easier to develop effective strategies to avoid risks if possible. The section concerning the level of supervision unveils possible ways to avoid risks or mitigate some aftermaths. This section is also instrumental in developing each department’s and the organization’s budgets.
Table 11. Lone Working Risk Assessment.
Security Staff
Pronto Courier is a small company with only around 50 employees. The major facilities are the warehouse, garage and the office. Clearly, these facilities need security staff. The company has a limited budget so a minimal number of employees will be hired. At that, the salaries for office security guards can be lower than those of the warehouse or garage security professionals. This distribution of money is relevant as office security guard may have the most basic skills as the employee can have the necessary training in the office.
Risks and the level of responsibility of warehouse and garage security employees are significantly higher, which translates into a higher salary. The conditions of work are also a bit different. As for the information security manager, it is important to hire as experienced professional as possible. The organization that is undergoing some changes needs a sound IS policy.
Reference List
Beaver, K. (2013). Incident response plan template: The essential elements. Web.
Business continuity management. (n.d.). Web.
Business continuity plan. (n.d.). Web.
Ispitzner. (2013). Awareness newsletters, posters, and blog posts – lame? Web.
Mcilwee, P. (2013). Business impact analysis. In K.B. Penuel, M. Statler & R. Hagen (Eds.), Encyclopedia of crisis management (pp. 84-87). Thousand Oaks: SAGE Publications.
Okolita, K. (2009). How to perform a disaster recovery business impact analysis. Web.
Ouch. (2014). Web.
Passwords are like bubblegum. (n.d.). Web.
The building blocks for a successful recovery program. (2014). Web.
Whitman, M.E., Mattord, H.J., & Green, A. (2013). Principles of incident response and disaster recovery. Boston, MA: Cengage Learning.
Winkler, I., & Manke, S. (2013). The seven elements of a successful security awareness program. Web.

