Introduction
This is a technical proposal for Shiv LLC Windows Network. The company will have three offices situated in Los Angeles, Dallas and Houston. In addition, it is growing rapidly and therefore it will require network scalability for upgrade. The Windows Network will account for the main staff at Dallas and Houston offices while Los Angeles sales people will require secure remote access to Houston office. It also highlights data security because of patent and trademark issues. Shiv already has the WAN connectivity with adequate bandwidth. The company will deploy Windows Server 2012 OS for its network solution.
Active Directory
Shiv will use a regional domain model in which all related data within the system will be copied to other domain controllers. The forest will have several users distributed across Los Angeles, Dallas and Houston offices connected by WAN. This strategy will reduce traffic replication over the WAN connections. A regional domain will be classified based on the company’s WAN connectivity.
The regional domain model will ensure that the company has a secure system setting for a longer period. State boundaries will be used to define domains. Any system categories in the organization could also be used to define the domain but this may be modified regularly and could need reorganization.
The regional domain model will bear a forest root domain alongside other models as may be required by the network. This process will account for possible future expansion of the company. That is, Shiv will determine additional domains that are needed to meet replication requirements, data isolation for sales team or service isolation for the main staff at the two offices.
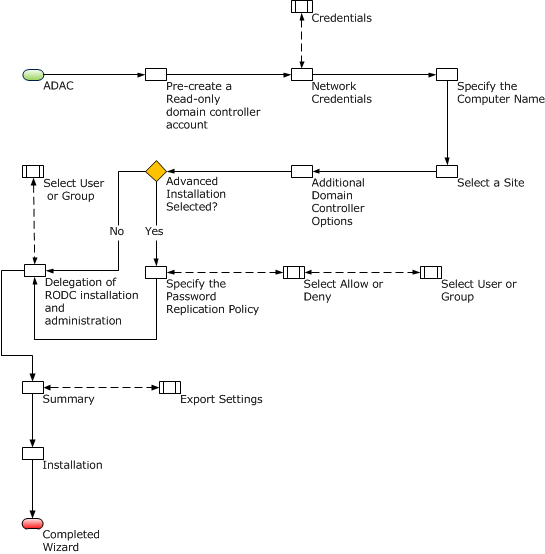
The domain controller will have a separate standalone server because of security concerns. It could however be expensive for the company to maintain. For effective duplication or transfer of data, the writable DC will be located at the AD DS location. RODC will not be in the same site with the writable domain controller because of security reasons. The site shall have the lowest cost site link to the site containing the RODC (Yu, 2010). In this context, the RODC replication accounts for the Bridge all site link alternatives, particularly with the writable DC.
Since the company’s current network will have few domain controllers, the initial placement of FSMO Roles could be correct. However, the company will consider new FSMO roles placement when the network expands. It will consider the PDC of the forest root domain because of the highest CPU usage and suitable hardware components in a consistent center site with the transfer domain controllers within the AD center.
The plan for AD backup and recovery considers the importance and mission critical role of the components. The company’s IT department must understand, implement and test effectiveness and reliability of the AD backup and recovery processes. Window Server Backup will be configured to provide a back up for the entire server and create a backup for system recovery. A bare metal recovery will be used in cases of hard disk failure. The situation may require a forest recovery plan for the Active Directory (Deuby, 2012). All DCs and failed forest will be considered in the recovery plan.
Group Policy
Shiv requires a Group Policy because of data sharing and security reasons, patent and trademark safety.
The Group Policy settings and Group Policy Preferences for Shiv will allow the company to manage certain configurations for users and computers in three different regional offices.
An Active Directory Domain Services (AD DS) environment through the Group Policy Management Console (GPMC) will be used to deploy applications within the Group Policy at Shiv. The Group Policy would ensure network security. This is a simple process involving a group action, which ensures that users see new installed applications when they login into the system. An administrator shall create MSI file before the system deployment to support other applications within the shared network. In addition, all authorized users shall have permission to share files and printers. The Group Policy would remain hierarchical. Therefore, the administrator shall be careful to ensure that established policies only affect the right users.
Shiv network system administrator will have the Remote Server Administration Tools to control settings from his or her desktop. In addition, the system administrator will consider all the 20 extensions that make up Group Policy Preferences for the company.
DNS
DNS namespace design shall be defined before the deployment of the DNS system. Internal namespace is recommended for the company so that it only remains accessible to employees within the internal network. An administrator shall maintain and manage all other functions.
Shiv shall have split DNS for Internet/intranet to eliminate administration burdens and system complexity involved in host configuration.
The second site will have DNS service for user login to reduce traffic directed to the VPN. Configuration shall allow users to gain access to the DNS Server, which would serve as the main DNS.
The company will have three zones configured for the network. Zones will have names of the DNS Server, IP addresses and other hosts within the network. The company will install more than a single DNS Server and therefore data consistency is necessary between the zones. DNS zone replication will be guaranteed between the servers.
The possible DNS Server zone types for Shiv:
- Primary zone is the major zone for writable DNS data. It would respond to queries from other servers and clients.
- Secondary zone will have the read-only contents of the DNS files. It will also be configured to respond to queries from other servers and hosts. The secondary zone will help in reducing traffic congestion on the company’s network and processing user requests in cases of failures at the main server.
- A stub zone will keep limited DNS data contained in the main server. The stub zone will assist in managing replication or transfer of traffic to the main server. The zone shall use local DNS cache data to resolve some queries from users.
The zone plan will consider DNS-related communication across the WAN. These may include server-to-server traffic from zone transfers and client-to-server traffic from query loads and updates.
The network of Shiv is likely to be large. It is therefore recommended to assess, test, analyze and review the three zone plans with regard to the noted behaviors on the network and traffic patterns. It is advisable for the company to partition and delegate DNS zones after a critical analysis of the traffic. This would result in an efficient and fault-tolerant network.
File and Storage Services
With the Windows Server 2012, the “File and Storage Services are automatically installed by default settings” (Murphy, 2013). However, the network administrator will be able to configure additional services as part of the Server (Murphy, 2013).
The company will enjoy scalability, availability and flexibility from the Server storage services. Shiv will protect its patent and trademark within the network. The network administrator will ensure that all security features and groups are effectively set. Users may gain access to files through various devices. Hence, there could be security breaches from various sources (Olsen, 2014). Window Server 2012 has additional features for File Services through Active Directory Rights Management Services (AD RMS). The network administrator will configure new security wizard to secure files within the server effectively.
Quotas shall be created to control volumes of folders and provide notifications when the storage capacity is exceeded. In addition, quotas will help in defining templates for any additional folders across the entire company.
FSRM would be configured to assist in managing data more effectively through File Classification Infrastructure. The File Management Tasks will allow the network administrator to use conditional action on files according to their groups. FSRM configuration would aid in providing reports on disk usage and information classification while file screens shall manage the types of folders that user can store on a file server. Finally, quota management shall allow the network administrator to restrict the space for folder storage and create quota templates for new folders and files.
DFS will be implemented. The namespaces will help the network administrator to classify shared files from various servers within the organisation. Configuration shall ensure that a single shared folder has several subfolders for convenience. DFS implementation will also ensure replication of files across multiple servers and sites at the company’s network. The remote differential compression (RDC) shall provide reports of any changes made to data contained in the folders and only replicate changes in the data rather than the entire folder.
Remote Services
Remote Desktop Protocol (RDP) shall ensure secure, managed remote access for users through RemoteApp programs.
Shiv will install Remote Desktop Services to enhance desktop functionality and application usage in any devices, virtual desktops, facilitate efficiency for remote sales team, create a secure environment for patent and trademark and ensure regulatory compliance. The company shall benefit from the use of virtual desktop resources, session-based desktops and applications. At the same time, users can conduct their activities anywhere and connect to organizational network or the Internet. In addition, the configuration will allow employees and the company to achieve the following practical services.
- Shiv will have unified administration control to monitor all virtual desktop applications, configure remote programs and add new servers from a single centralized site.
- Clients will have individualized setting across the organization and use shared virtual desktop apps and system resources at different sites.
- The system shall require relatively affordable storage because of restricted storage supported with live relocation of collections across the network. In addition, user virtual desktops will use storage on the common network within the organization.
- The network administrator will create a pooled virtual desktop management system. Therefore, any required changes, updates, security changes and new installations can be managed virtually from a single central site.
WSUS
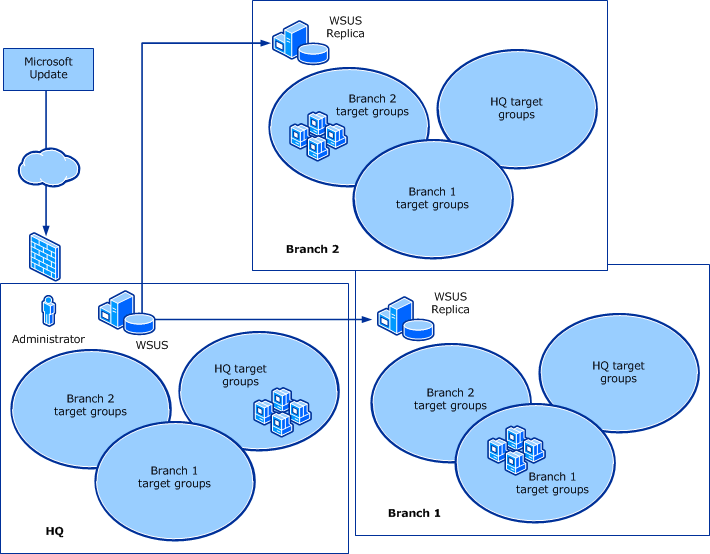
The WSUS server will provide the necessary features that the company’s network manager requires to control and allocate updates within the entire network. Moreover, the WSUS server (an upstream server) will act as the source of updates for other servers within Shiv. The main WSUS server will be linked to Microsoft Update to ensure regular access to newly released updates and necessary data. Shiv network manager will assess network security and designs and verify the exact number of WSUS server updates that can directly link to the source of updates.
The system administrator will control the deployment and maintenance of released software from Microsoft Updates within the company’s network. The WSUS shall provide operational efficiency, protect the network from security vulnerabilities and ensure system stability.
Shiv requires a higher level of the network security because of patent and trademark. If the company will fail to establish and keep system security and acknowledged levels of trust, then the network may be exposed to several threats and vulnerabilities, which could be easily exploited by hackers and staff. As a result, Shiv will suffer revenue and intellectual property losses. Shiv must therefore curtail network security weaknesses and threats through updates and ensure an appropriate design of the OS, run the most recent software and use only suggested updates from Microsoft Update. Shiv network administrator will ensure the following core environments to derive maximum business value from WSUS.
- Centralized update system
- Update management automation
New servers shall be deployed in the Replica mode to achieve centralized administration by sharing updates, approval status and groups throughout the company’s network.
Summary
This technical proposal for Shiv LLC shows that the company will rely on features available on Windows Server 2012 for its network. The company will leverage Windows Server 2012 capabilities, flexibility, availability and scalability to ensure reliable and secure platform for its operations across the three offices.
It is believed that Windows network will be easy to implement, run, maintain and deploy in new locations. In addition, it will offer cost advantages to the company.
References
Deuby, S. (2012). How Windows Server 2012 Improves Active Directory Disaster Recovery. Web.
Murphy, I. (2013). File Services: a new approach in Windows Server 2012. Web.
Olsen, G. (2014). Secure Files in Windows Server 2012 with Active Directory RMS. Redmond Magazine. Web.
Yu, P. (2010). RODCs: Understanding and Implementing the New Windows Server 2008 R2 Domain Controllers. Redmond Magazine. Web.
