Overview of the Hampton Specialized Medical Center
The Hampton Specialized Medical Center is a facility that offers health services within the state of New Jersey. The center has two other branches spread across New Jersey. The company has been in business for more than fifteen years and is currently a leading lifestyle ailment management facility. Specifically, the center has interests in wellness programs, preventive care, and management of common ailments. The center has about 1,800 employees working across its three branches. The head office has the highest number of employees standing at 420. The health center offers comprehensive lifestyle ailment management, counseling, and treatment services to residents of New Jersey and beyond. The hospital is also a key research center with a fully-fledged laboratory and an action patient data management department. The center has five departments with specialized personnel to manage each category of services. Specifically, the facility is divided into the health records, finance, operations and information technology, research, and healthcare departments.
The facility has a complex operational model comprising of quality assurance and control. The operational strategy aligns the desires for quality and optimal functionality at the least possible cost. At present, the quality management strategy has been very instrumental in ensuring that adequate service provision is aligned with the goal of proactive customer engagement. The hospital has a fully functional information technology office under the operations and information technology department. The information technology office is tasked with managing the communication and information sharing within the head office and the other two branches. The hospital has a relatively secure intranet network and active online platform where all activities are facilitated. The system has been very effective since doctors can track previous treatment records and access the current files just by clicking a button.
Despite the proactive information sharing facility, the facility is currently facing the threat of a weak information security system since there are several loopholes that can make it vulnerable to external intruders. For instance, a doctor is able to access the information sharing platform of the facility even when outside the facility. Besides, the information technology network has only two layers of protection in the identification of persons authorized to login into the system. The two layers only help in verifying personal identification information rather than the intention of the person login in. Therefore, there is a need to present a secure and policy-backed information management module for Hampton Specialized Medical Center to avoid potential infiltration into the facility’s information data system. The report presents a comprehensive information security policy, enforcement strategy, support tools, and necessary compliance module. Specifically, the report presents a contingency planning strategy to ensure the above-mentioned challenges are addressed to improve the Hampton Specialized Medical Center’s overall security and preparedness.
The significance of Developing the Contingency Planning Efforts
Since Hampton Specialized Medical Center operates in the healthcare provision environment, which is characterized by the need for efficient and effective information protection, contingency planning would ensure that the current loopholes in its information management system are sealed. Moreover, contingency planning would present immediate response, restoration process, and prevention of similar incidents in the future (Dasgupta, Suar, & Singh, 2013). Specifically, contingency planning captures the incident response planning (IRP), disaster recovery planning (DRP), and business continuity planning (BCP). With proactive contingency planning the Hampton Specialized Medical Center’s information management system will be in a position to detect potential information breach threats that would otherwise compromise the availability, integrity, and confidentiality of the facility’s activities.
When applied at Hampton Specialized Medical Center, contingency planning as a program will ensure that there is a continuous assessment of potential information breaches and prioritizes each breach onto the attack profile template (Australian Curriculum, 2015). In the end, the Hampton Specialized Medical Center will improve its efficiency and confidentiality its management of information sharing system.
Contingency Plan for Hampton Specialized Medical Center
In the case of Hampton Specialized Medical Center, the proposed contingency plan is aimed at ensuring business continuity management. This plan aims at interweaving the disaster recovery and business continuity planning (BCP). The proposed plan is created to develop a clear contingency planning statement, review of business impact analysis, identification of preventive controls, development of possible recovery strategies, creation of an information technology contingency plan, testing the plan, continuous employee training, and strategies for maintaining the plan (Grant & Meadows, 2016).
Since the contingency plan is modeled around business continuity, it is important to identify strategies that can be applied to sustain critical operational systems at the Hampton Specialized Medical Center. This is necessary for reducing outage time while optimizing operations (Grant & Meadows, 2016). The proposed contingency plan will adopt the following steps as summarized in figure 1.
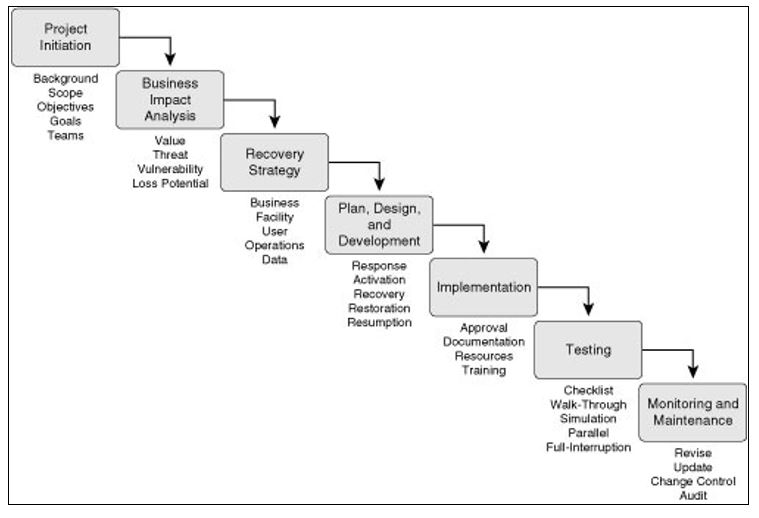
Step 1: Project Initiation
Before the commencement of the BCP, it is vital to create a strategic management support. This is achievable through the education of the Hampton Specialized Medical Center’s management on the significance of accepting the BCP. For instance, there is need to design and present a management seminar on the current risks the hospital is facing, potential threats to its information management system, and relevant costs of potential damages from such threats and risks (Hollier, Murray, & Cornelius, 2008). This step prepares the management for taking responsibility and owning the final plan. Involvement of the management also ensures that budget allocation for the contingency plan is adequate.
The management should endorse a leader to spearhead the process of bringing all the stakeholders in relation to the recommendations and plans of the BCP. This is achievable through the creation of an action plan to encourage teamwork among the management representatives, information management department, legal personnel, and other business units on a need basis. In order for the planning to be effective, the inclusion of the shareholders through a representative would make the execution stress free (Hollier et al., 2008).The next step is the scope definition to maximize the general effectiveness of the BCP plan. It is important to accommodate office politics and avoid any project creep that might undermine the original plan by delaying completion. As a part of the contingency mitigation, adherence to the set time schedules, resources, budget allocation, and success factors will make the process flawless (Grant & Meadows, 2016). The following responsibilities will be allocated to the team.
- Identification of the legal and regulatory laws that should be complied with
- Identification of the potential risks and threats
- Estimation of the level of these risks or threats in order to correctly identify cost implications
- Carrying out the BIA
- Prioritizing the risks or threats
- Creation of the steps to resume vital business functions after a disaster
- Allocating duties to employees during and after a crisis
- Documentation, communication, and training as aligned with the contingency plan
In the initiation stage, it is critical to align the BCP to the organizational culture on threats and risks as a detective and preventive controls. Specifically, the above roles should be executed in a way that encourages preventive, detective, and corrective controls for identification and restoration to normalcy after a threat has been detected.
Step 2: Business Impact Analysis (BIA)
This step involves the implementation of a BIA to measure the actual impact of a potential threat on the critical functions of an organization. In the case of Hampton Specialized Medical Center, the BIA stage considers each of the identified threats and their implications in order to draw a mitigation plan. For instance, although the threat of misconduct on the side of the authorized personnel using the information sharing system, it does not disqualify any planning to reduce any potential impact should such an incident arise in the future (Grant & Meadows, 2016). In order to accomplish BIA at the Hampton Specialized Medical Center, it is vital to look into possible threats, the risks posed by these threats, severity of impact, and possible losses. In this scenario, it would be productive to prioritize operation that would quicken the recovery planning. As captured in table 1, the following framework will be used in the BIA for the Hampton Specialized Medical Center’s information management contingency planning.
Table 1: Framework for developing the BIA
(Source: Hollier et al., 2008)
The framework should be accompanied by a series of potential scenarios to paint a clear picture of the immediate response mechanism for continuous operations. There is need to use effective data gathering tools such as the SunGard Paragon and Strohl Systems BIA Professional software to automate the apportioning of the collected data (Jiawei, 2013). In the case of the Hampton Specialized Medical Center, as captured in table 2, the following steps will be involved in the BIA.
Table 2: Steps involved in the BIA
(Source: Jiawei, 2013)
This stage is completed with a comprehensive assessment of potential loss through the use of the BIA questionnaire. In this scenario, a questionnaire may be developed to probe the views of end-users on the real loss of an information breach. As captured in table 3, the responses can be graded in terms of low, medium, high, and critical (Jiawei, 2013).
Table 3: Grading of questionnaire responses
(Source: Scherer & Stefano, 2014)
Step 3: Recovery Strategy
The recovery strategy is the predefined action plan approved by the management in the event of disruption of normal operations following the occurrence of a threat. As part of the mitigation strategy, the appointed team is mandated with the duty of completing and evaluating;
- Details of documents on costs for each response alternative
- Quotation of estimation of costs for external services that should be procured
- Written contracts with selected external information system vendors
- Resumption strategies in the event of a complete shutdown of the system
- Details of documents on findings and recommendations on the chosen mitigation strategy for approval and feedback
In order to make a decision on the most appropriate recovery strategy, the team should consider the business recovery process, facility recovery, user recovery, operations recovery, and information or data recovery. In the case of the Hampton Specialized Medical Center’s information management contingency planning, the business process recovery is streamlined within the listing below.
- Is the current system prone to external infiltration?
- Which point(s) of weakness can be identified within the system?
- What can be done to strengthen these weak points?
- Is the system capable of recovering from the potential threats identified?
- What is the cost of restoring the system in case of a threat incidence?
This part is followed by the generation of the actual organizational functionality in the recovery time to ensure that the impacts of any information breach do not compromise the vital organization function. As captured in table 4, facility incident response and recovery is aligned with multiple backup and restoration aspects.
Table 4: The timeline for incident response and recovery process
(Source: Grant & Meadows, 2016)
In order to address potential interruption from an information breach, the Hampton Specialized Medical Center’s information management should use the mean time to repair (MTTR) and mean time between failure (MTBF) to establish the lifetime of the system and the duration taken to restore the network. In order to protect the current Hampton Specialized Medical Center’s information management network, there is need to activate diverse routine, alternative routing, last mile protection, and voice communication recovery.
Lastly, as part of the information and data recovery, it is prudent to use backups, remote journaling, and offsite storage. For instance, it is possible to use digital audio tape, quarter-inch tape, and CRD media for temporary storage. Since Hampton Specialized Medical Center has a complex information sharing system, it would be ideal to apply full backup, incremental backup, differential backup, and continuous backup. These backups should be kept away but accessible in case there is a need for a restoration. In order to make the system secure, the Hampton Specialized Medical Center’s information management department should opt for electronic vaulting, remote journaling, database shadowing, and storage area network. These options are ideal for ensuring that the recovery point (ROP) and recovery time (RTO) objectives are met.
Step 4: Design of the Plan and Development (Incident Scenario)
At this point, the contingency plan begins to take shape. Basically, the appointed team is expected to develop and design a recovery plan for business systems that are critical. At present, Hampton Specialized Medical Center is not fully prepared to handle any major information system breach since there are only two layers of security. Therefore, there is need to plan for such occurrences to minimize their impact on the security of information at the facility. Basically, the proposed plan will act as a guide in the implementation of the contingency policy. In this scenario, the objectives of the plan include:
- Identification of the priority and critical functions for restoration.
- Identification of the support systems for the critical functions.
- Estimation of the current threats in order to compute the appropriate resource allocation for recovery.
- Selection of the most appropriate recovery strategies, systems, personnel, and necessary equipment.
- Computation of the monetary needs and appropriate management strategies to foster the recovery process.
In the event of a security breach, the first step would require personnel mobilization by contacting the relevant employees through the use of outbound dialer or call trees. These systems are capable of call rollover, alert users of a call back request, and capture a recorded message. In addition, email server and mobile phones can also be used to mobilize personnel. The second step is a consultation with an external expert or group. This process has a protocol of command to ensure that there is a flow of information for any intervention strategy. This step is vital in managing the situation from blowing out of proportion or misreporting of the occurrence. There is a need for Hampton Specialized Medical Center to take an insurance policy to cover potential losses as a result of a breach of the data center. In this case, the facility should consider the hacker insurance, software recovery, outages, and documents or records covers.
Following this action plan makes the company well-equipped to face any kind of information security breach as it allows for a prompt response through the established set of actions that are enumerated above. The research in the sphere of medical informatics and practical application revealed that the following contingency plan generally corresponds with requirements for security, applicability, and effectiveness (Sittig, Gonzalez, & Singh, 2014).
Step 5: Implementation and Policy Framework
The implementation process involves awareness creation to ensure that the stakeholders embrace the policy. This is necessary to promote policy ownership and minimize potential inter-personnel conflicts. In this scenario, there is a need for a training session on how to handle an occurrence of any threat in the information management system. Approval of the management is also required before carrying out the awareness promotion program. The training program should encompass expected behavior, response strategy, and channel for communicating any unusual event. As part of the awareness training, there is need to further equip personnel with specific response tasks with the right skill and equipment to quicken the recovery process.
Step 6: Testing
The final step is testing and maintenance of the BCP. However, the awareness training should continue. It is vital to test the plan to authenticate its applicability. In this scenario, the testing should be done at least twice in a year. Testing should run from the easy to difficult parts. The focus should be on systems supporting the core processing at a time when such operation has minimal disruption to the facility functions. Since the Hampton Specialized Medical Center’s information management system is not complex, the use of checklist, structured walkthrough, and simulation would be ideal tests (Stephenson, 2013). Under the checklist test, the relevant departments will go through the list and make sure everything is okay before executing the plan. Consequently, there is a structured walkthrough in a boardroom conference where the relevant personnel reviews each line in the policy (Scherer & Stefano, 2014). Lastly, simulation involves drills by the response team on how they would react to an actual occurrence of the threat up to the point of complete recovery. This is necessary for verification of the ability of the team to effectively use the current tools and equipment to respond to any threat.
Step 7: Monitoring and Maintenance
It is important to define clear job descriptions, performance reviews, and audits to ensure that the maintenance process is institutionalized. As captured in table 5, the BCP process responsibilities determine the success of the entire contingency plan.
Table 5: BCP process responsibilities
(Source: Grant & Meadows, 2016)
Ethical Concerns and Ramification
The primary ethical concern is the possibility of human interference, especially if such occurrence is instigated by a member of the implementation team at the hospital. This would negate the contingency planning efforts since such party is expected to stick to the professional and ethical code of conduct (Stephenson, 2013). However, such a situation is easily rectified on its own once the user logs off. Then a report will be automatically generated and forwarded to the CP team leader. Planning for this concern involves the creation of a backup and quick system restoration cache to ensure that potential consequences are short-term and relatively harmless (Scherer & Stefano, 2014).
References
Australian Curriculum. (2015). Applying social and ethical protocols and practices when using ICT. Web.
Dasgupta, S. A., Suar, D., & Singh, S. (2013). Impact of managerial communication styles on employees’ attitudes and behaviours. Employee Relations, 35(2), 173- 199.
Grant, E., & Meadows, H. (2016). Communication technology update and fundamentals (15th ed.). New York, NY: Routledge.
Hollier, F., Murray, K., & Cornelius, H. (2008). Conflict resolution trainers’ manual (2nd ed.). Chatswood, NSW: Conflict Resolution Network.
Jiawei, H. (2011). Data mining: Concepts and techniques (3rd ed.). New York, NY: Morgan Kaufmann Publishers.
Scherer, M., & Stefano, F. (2017). Assistive technology assessment handbook. London, UK: CRC Press.
Sittig, D. F., Gonzalez, D., & Singh, H. (2014). Contingency planning for electronic health record-based care continuity: a survey of recommended practices. International Journal of Medical Informatics, 83(11), 797-804.
Stephenson, M.O. (2011). Considering the relationship among social conflict, social imaginaries, resilience, and community-based organization leadership. Ecology and Society, 16(1), 1-3.
