Introduction
Current technological advancements demand that Goodyear, and other organizations develop human-like machines to work autonomously and imitate a person’s cognitive behavior. Progresses in AI and managerial interests have sparked a hype in many firms to invest heavily in capitalizing on technology through their operations. However, there is little academic information to support the implementation of AI among nay managers, leading to undesired results and project failure (Reim, Astrom, and Eriksson, 2020, p. 180). AI is associated with human cognition with similar attributes such as reasoning, language, problem-solving, understanding information and other characteristics. Most companies experience enormous development challenges in implementing this technology despite being the primary commodity in current generation businesses. This plan focuses on developing an AI framework for Goodyear based on various assumptions.
Projects Objectives
This project aims to implement expert system at Goodyear Tire Company based on various assumptions. Through the system, the project will centralize decision-making processes in the company, integrate diverse human expert intelligence, reduce the number of human mistakes, avail diverse information, and increase efficiency. It will also enable the company provide strategic advantages that it may use to outcompete rivals.
Organizational Objectives
Goodyear aims to increase the value of its products for everyone using market-driven innovations. It also anticipates delivery of high-quality tires, as well as related services and items for their customers. Its common goal is to act, develop, motivate, and retain the best workforce, earn and establish durable relationships with customers, business partners, consumers, and suppliers beyond their expectations (Goodyear Corporate). Goodyear aims for excellence and efficiency in the organization, creating a sustainable business framework that continuously earn competitive returns on investment (Goodyear Corporate). With its shared values, the company seeks to support wellness and safety, apart from caring for the environment and fostering team-based culture of continuous development.
Project Scope
Project identification was the first step of this research, where the company was identified and the need to implement AI software in its operations. Afterward, stakeholders met to discuss the project requirements and plan for the whole activity. Expert system users will be trained on various requirements, usage procedures and security issues. The stakeholders will install the hardware and later test it to ensure interaction of the system’s elements with the environment, including databases, final users, and other information platforms. Afterwards, they will obtain certification and approvals from relevant authorities. Software testing by the software engineer will follow this step to determine prototype deficiencies in performance.
Project Assumptions
During the expert systems implementation, stakeholders assume that there is reality and comprehension in data representation and storage. The information should be retrievable according when needed as well. There are judgements concerning the truthfulness of given datum. Stakeholders minimize the input of information into databanks and focus on true statements. The developer considers the degree of data certainty and accept less than 100% probability. Rules are also developed to be used in developing recommended planning decisions. Another assumption is the information used to generate recommendations for planning and design. Such data is based on the theory of linguistics and logic. It is assumed that the system is strong, reliable and efficient.
Project Roles and Stakeholder Responsibilities
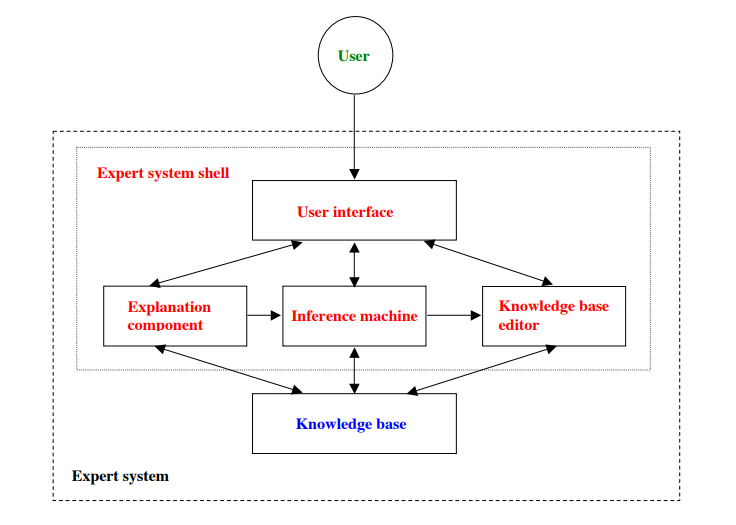
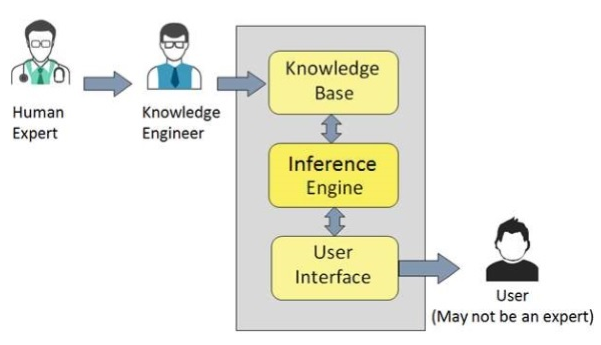
Expert system works in an expert role to support users of the proposed actions from the framework. It could serve as a communication and translation device between different interfaces, or perform knowledge accounting while keeping past information on decision-making processes. It stores each process into a file that engineers can later look at. From this information, the engineer can identify repetitive problems that might necessitate a revision of the entire procedure. The system also troubleshoots operations and respond accordingly, apart from using knowledge synthesis ability to acquire information that can facilitate other expert systems or employees to analyze particular data. In an organization such as Goodyear, the system will acquire a wide range of data and present them in a coherent manner to the maintenance department. It will enable the department to detect switches that are likely to fail and send warnings to technicians. As a result, the company would not have to acquire raw data for detecting possible failures. Figure 2 shows expert system configuration while figure 3 shows a framework of expert system participants. Participant responsibilities in the system include (Javapoint, no date):
- End user: an individual who acquires advice from the expert system, and the information cannot be obtained directly from the expert.
- Domain expert: an individual whose knowledge and expertise is seized to develop and expert system.
- Expert (knowledge engineer): an IT technician who uses his skills to integrate knowledge from domain experts into the computer system.
Timeline
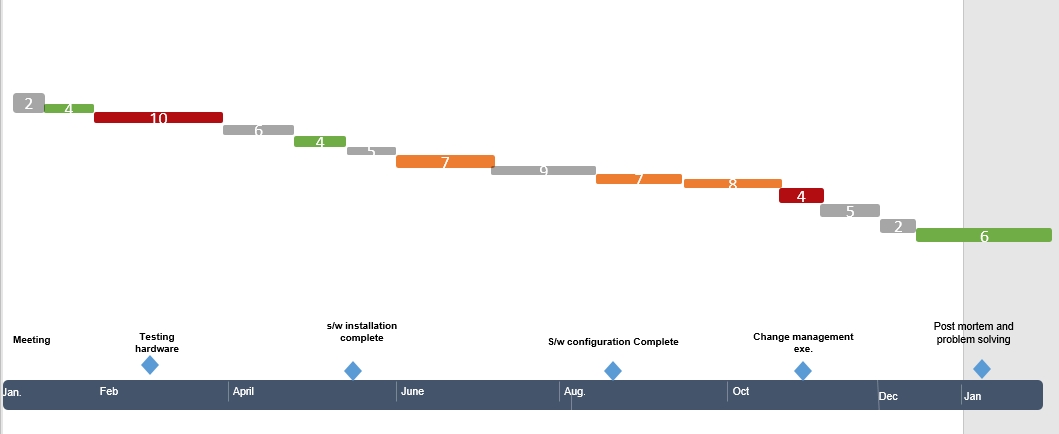
Figure 4: Activities
The activities will be completed as shown in the following diagram. Some assumptions were made to prepare the Gantt diagram.
Risk Management
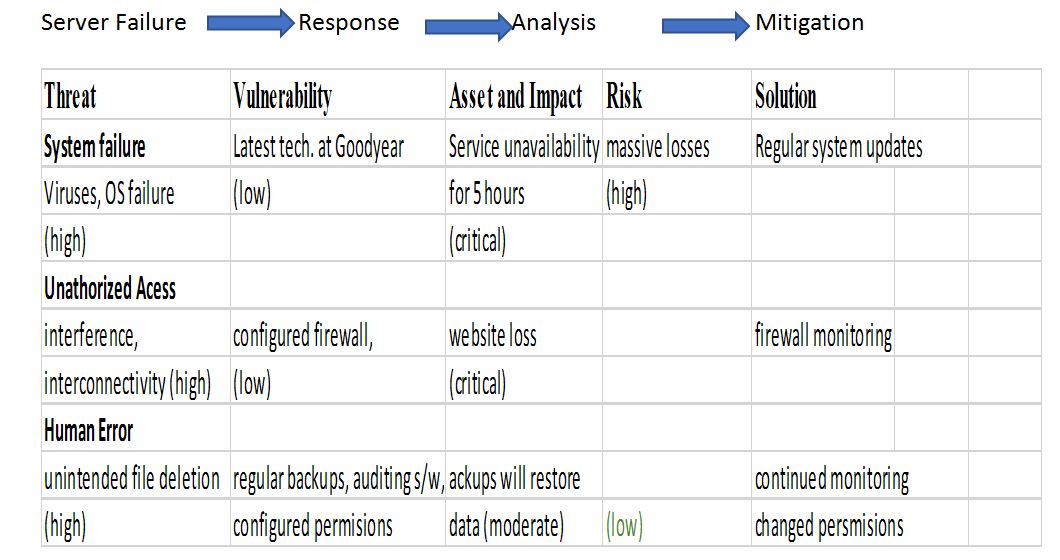
The project necessitates a risk management framework to ensure its sustainability. The framework will reduce maintenance costs and prevent extreme conditions that alter company operations. Each risk will have a solution to be applied hastily since expert systems should respond quickly. The framework will entail seven steps, the first including the determination of valuable assets. The researcher identifies such factors across the company that could be vulnerable to threats, leading to financial losses. For example, they could identify vulnerable websites, servers, buyer credit cards, client contact information, customer information, trade secrets, and stakeholder documents. Second, the researcher should identify the possible consequences of the threats. This could be achieved by estimating the financial losses that the company could receive following damages to particular assets. The most common consequences include system failure or downtime, data loss, and legal consequences that the company could end up paying for.
Moreover, the researcher should identify particular threats and rate them at different levels. The issues include anything that might damage vulnerable assets, breaching the company’s security and causing harm to its assets. At Goodyear, threats could include application downtime, natural disasters, malicious attacks by humans through interception and interferences of system performance, as well as accidental workforce errors. The fourth step is to identify risks and assess the possibility of their exploitation. This stage deals with the weaknesses that permit threats to infringe a company’s security and harm assets. The researcher should look at what will protect their systems from particular threats, and determine the chances that they will actually damage the assets if they occur. Some of the vulnerabilities to determine in this project include human factor, software design configuration, and equipment flaws.
Risk assessment will follow threat identification and it involves assigning those values whether they are high, moderate, or low. Afterward, solutions development will follow for every high risk, and moderate ones, along with approximation of their costs. Creating a risk management plan will then follow, after which a strategy for information technology infrastructure will be created to mitigate the most significant vulnerabilities. Further, defining mitigation processes will be necessary because the company can only strengthen its security infrastructure but fail to avoid risks. The process involved determining why a disaster occurred, and trying to prevent their future occurrences, apart from reducing the intensity of its consequences. The process is as follows:
Stakeholder Management
There are many people affected by the company’s plan and some of them have the power to bar or advance the work. Others would be interested in the project, while others do not care, calling for the need to prioritize them. In this project, stakeholders are mapped out according to their power over the project’s task and their desires. Figure 5 shows power versus interest grid to manage stakeholders. The position that each stakeholder is allotted on the grid shows the appropriate steps to take with him or her.
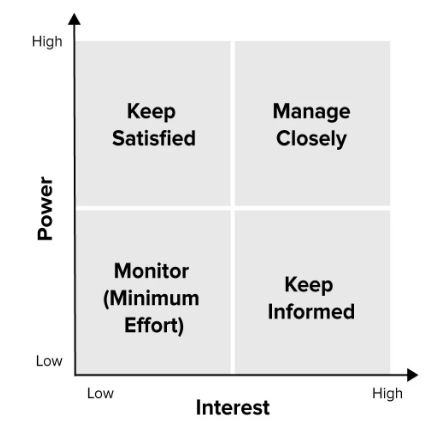
High power with high interests implies that the people are highly concerned with this project and they should be managed closely by fully engaging them and imputing excellent efforts to satisfy them. The slot with high power and low interests imply that the stakeholders need to be kept satisfied by using just enough efforts but not going an extra mile to bother them with the idea. Furthermore, the slot showing lower power and highly concerned stakeholders shows that they need information. The researcher will only offer adequate information to these people and engage them to ensure that they prevent major issues from arising during project implementation. Lastly, the quadrant showing lower power and slightly interested people demonstrates the need to monitor such stakeholders and avoid bothering them with too much information.
Project Funding
This project’s stakeholders have been developing expert systems and other saleable software. They will therefore generate revenue for the ongoing project from monthly subscriptions, sales commissions, registration charges, sale of software and hardware as well as through promotional programs. The partners will also offer organizational automation services to earn income. Training interested people will also earn some money to facilitate the project. The partners will be offering data back remedies at a fee to generate income. Friends and family members will play a crucial role in contributing this project’s startup capital. Personal savings and loan from bank will form 50% of the revenue required to actualize this project.
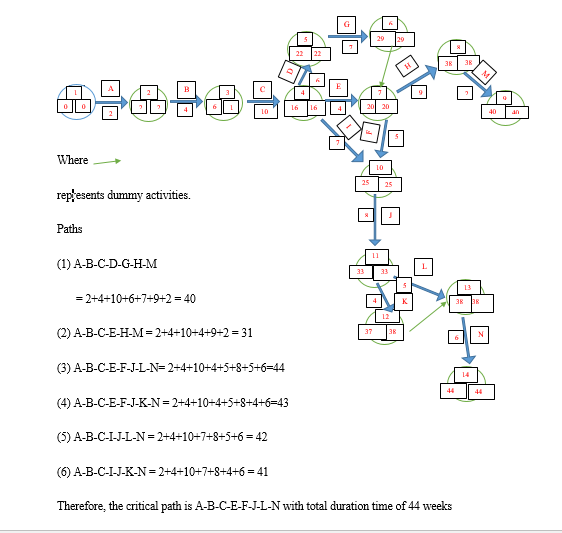
PERTH Diagram Showing the Critical Path
The critical path refers to the longest sequence a task will take to be completed successfully. The tasks in this path are critical activities because any delays will prolong the project. Identification of the critical path enables the project manager to determine the total time the project will take. It is crucial to calculate this path during the project-planning phase to ensure that significant deadlines are met and critical tasks are completed systematically. Figure 8 shows the Perth diagram that was used to determine the critical path for this project. Critical activities will take 44 weeks, making the crucial path in the project.
The critical path method has disparate drawbacks, making unsuitable for the project. The method is ineffective in handling projects, which share available resources. Moreover, the framework fails in case there are changes in the task precedence and sequential links among activities (Reim, Astrom, and Eriksson, 2020, p. 183). Vast information is required to create an effective plan, which can become too costly. It is recommended that tasks be prioritized in this project to avoid challenges associated with critical path method. A clear understanding of project timeline intervals will enable the researcher to reduce the time required to complete individual tasks. Comparing the plan and actual progress will ensure that implementation errors are minimized. Risk assessment throughout the project will enable the researcher to determine preventive measures. Staying focused on core activities will ensure that each task is completed within the specified time.
Conclusion
This project aims to implement expert systems management at Goodyear Tire Company. The main sources of finance include personal savings, loans from bank, friends and relatives, sales, and website subscription fee. The critical path method was applied to determine the duration of the project, which 44 weeks in the critical path. This method is inefficient because it does not permit changes in task precedence, apart from not favoring the assignments, which require similar resources. The researcher should stay focused throughout task completion to ensure that the critical ones receive a considerable attention.
Reference List
Goodyear Corporate. (no date) Workforce safety and health. Web.
Reim, W., Åström, J. and Eriksson, O., (2020) ‘Implementation of Artificial Intelligence (AI): A Roadmap for Business Model Innovation’, AI, 1(2), pp.180-191.
