Introduction
Recent world is growing very fast and new and new changes are coming up with short intervals. Now there are many medium for travelling and load lifting but still shipping industry has its own significance. This world has become modernized but shipping industry is one of the most significant medium for traveling and load lifting over long distances. According to one survey, around 90% of the trade across the world is done by the international shipping industry.
Without using shipping medium trade could not meet the standards. A huge proportion of import and export is done by shipping as shipping expenses are less as compare to other travelling mediums. Without shipping trading of goods required for the modern world could not be possible. Numerous trade companies are now working in this vein and brining new and advance mediums for trading of commodities (Flag State Performance 2006: 1).
Several countries continue to amplify bringing new advantages for users worldwide through competitive cargo costs. Everyone is thankful to growing efficiency of shipping industry as one of the best transport mode and it has increased economic relaxation, the aspects of growth in shipping industry is still high in upcoming years.
According to an estimate, around 50,000 merchant ships are offering trading services internationally, and they offer transport of every kind of cargo. The world swift is now recognized in over 150 nations, and over a million tars from every nationality. There are thousands of ship merchants, few are listed below:
- Container Ships.
- Bulk carriers.
- Tankers.
- Ferries and Cruise ships.
- Specialist ships.
Container ships
Container ships usually use to carry manufactured goods and products, and they travel according scheduled liner services.
Bulk carriers
Bulk carriers usually carry load of raw materials like coal and iron ore.
Tankers
Tankers are widely used for transportation of crude oil, petroleum products and chemicals. Tankers are use worldwide for various purposes.
Ferries
Ferries are usually used for short journeys with less weight with a combination of mix passengers, cars and several other commercial vehicles. There are thousand forms of ferries which provide easy accessible way to travel.
Specialist ships
Specialist ships and cruise ship demand has grown a lot in recent days. During 1980, demand of cruise ships has expanded a lot as it has luxurious hotels and many other facilities like supply vessels for the offshore oil industry, anchor handling, salvage tugs, ice breakers and research vessels.
There is a long route for world economy to grow, especially in some Asian countries (THE ROLE OF THE FLAG STATE IN SHIP FINANCE, 2009: 1). Many developing countries follow the same pattern such as economic growth is accompanied by the rapid expansion in international trade and consumption of energy like development pattern which demonstrates a challenge to the shipping industry and the marine industry.
Nowadays, oil transport has enlarged a lot and million of oil tanks are being transferred from one place to another on daily basis. The increase of oil transport will highly affect new developing countries for instance Asia, China, India and Vietnam. The low cost of transporting goods by sea is always attractive for consumers. in the mid of 1980, the world trade value has grown up to 12% per year, where as total freight costs during this period has raised up to 7%, presenting the fall in unit transportation costs (SHIP MORTGAGES AS A FINANCING VEHICLE: THE FLAG STATE’S ROLE IN PROTECTING THE SECURITY INTERESTS OF LENDERS, 2009: 1). More over, analysis carried out by UNCTAD states that the ratio between freight cost and import value costs is less than 6% of the import value of user’s goods.
The low cost of maritime transport also contain a great attraction for consumers. In recent years shipping industry has gained record markets and freight costs for consumer goods have recorded a small portion of the shelf price, and continuous changes will bring a huge development in shipping industry in upcoming years. In today’s shipping industry the most significant problem faced by thousands of owners is open registry. Open registry is one of the hottest issues in shipping industry.
“A good international safety & environment protection legal, regulatory and operational framework is in place. Such framework needs to be maintained, improved and strengthened, continuously and rigorously. China, India and most other countries have been involved in making and maintaining a safer and cleaner maritime transport, they should be more integrated. These new players do realise the stake and importance, for their own interests, to have an environment friendly and sustainable maritime transport system” (Shuo Ma).
There are thousand of organizations that have been established, in order to increase the safety and security in crews. They are working for enhancing the standards of safety and crew conditions. But, despite developments of rules and regulations the registry problem still resides. Beside registration, ship industry faces five core issues in real world which are listed below: Bulk Carrier design and safety, Port State Control, Mississippi Towage, The safety of terminal loading and discharging operations, Flag issues , Environmental protesters, Education and training, Security and the dry bulk industry.
Flag issues and environmental protesters are the two biggest problems out of five faced by shipping industry (Shipping Industry Guidelines on Flag State Performance 2006: 45). Flag issues shipping industry and ship owners face a huge problem related to flags and registries nowadays.
A key responsibility of a flag State is to enforce the convention standards on ships and crews which are already registered. While choosing a flag ship-owners, some factors need consideration for effective output. Considering those factors a diplomatic and administrative support is required, port and cargo need special consideration in all aspect at early stages preference schemes and fiscal issues require consideration too. A Port States traditionally use as a ‘flag’ a flag is considered as a agent for ship targeting for auditing and MOU’s maintain ship custody records and publish ‘black lists’ of the worst flags performance which is highly based upon three-year rolling statistics (Toweh 2008: 1).
Intercargo’s bulk carrier lists includes flags like Panama (29%), Liberia (8%), Malta and Cyprus (9%) and China and Greece (6%). Most frequently used flags introduced by Intercargo members include Panama (31%), Hong Kong (9%), Liberia (11%), Greece (6%) and China (7%). Security and safety are two main concerns of maritime business the issue of maritime security has gained a considerable coverage amount since the 9/11 attack in United States in September 2001.
At the IMO, the issue of maritime security has been gained a lot of popularity and has been debated. In December 2002, maritime security acquired a sequence of maritime security commissariat for all type of port facilities and over 500 GT ships which acceded in 2004 for developing a strong strategic plan certain things need an action, a company needs to hire a security Officer will need to be hired, and ships will need to be fitted an Alert security System and carry a Continuous abstract record to list all its flag, ownership and classification details (International Transport Workers’ Federation. “FOC Countries 2009: 2).
Definition
The Flag State choice holds a great significance and with the passage of time it has become an important issue in the last few decades due to rigid international rules and regulations, mingier port state give control to a ship owner of available flags on a ship. Now the main question arises does a vessel’s registry flag matter? Do ship owners and lenders, covers finance vessels based on the Flag State?
The honest answer to all of these questions is yes, but above question only shed light on just a few issues which must be considered and reviewed by a owner while selecting a Flag State from any financial institution when sponsorship is a vas. The main objective of international lending institutions in a Flag State should be at first priority that a ship owner must go for flag registry first. Banks usually do not like lend an advance funds. A ship travels from one port to another port, a Flag State adds nationality to that particular ship, and hence ship protection to all those financers who sponsors it, choosing a flag an exclusively important decision. Therefore, it is significantly important to recognize some of the important qualities which a ship owner must check and asserts while considering a Flag State.
“When a ship is registered in a particular country (the ‘flag state’), the ship and its owner become subject to the laws of that state. Registration makes the ship an extension of national territory while at sea. It also qualifies for its protection.” (Stopford).
Shipping is one of the safest modes of transport. There is one most easy concern about shipping companies’ use of flags need special consideration that may not follow fully with international standards & regulations. Moreover, modern worries about maritime safety & security have added a new angle to these concerns (Carlisle, Rodney 1981: 43); it’s a primary responsibility of shipping companies to find out new ways for the safety of their ships and crews. The flag state plays a pivotal role in the safety and security of ships and crews. It performs a significant role with regard to the life security, protection of the marine surroundings (Regulatory Framework, 2009: 1).
It’s a primary objective of flag to control, implement and enforcement of international rules and regulations in all ships ‘flying its flag’. Strong and effective rules and regulation by state government are designed and implemented in order to ensure the safety and security and pollution-free ship operations of the ships and crews. The United Nations International Maritime Organization (IMO) has observed that most ship owners were loosing faith on flag state. Keeping in mind the losing faith factor IMO has designed a plan and strategies in order to restore confidence in the flag state (VESSEL REGISTRATION AND MORTGAGE RECORDATION PROCEDURES, 2009: 1).
There is also a strong need to promote satisfactory flag state performance, in order to restore consumer’s confidence and ship owner’s faith in the flag state. IMO also have a strategy to discourage the use of flag that perform below the international standards.
The regulatory role of the flag state
Once registered, a ship becomes a part of sate legal services. After registration, a ship becomes a part of legal purposes. The flag states holds several responsibilities, it poses a primary legal responsibility of dealing with common security threats.
Flag states are mainly responsible for security and safety of the ships. They pose a responsibility of approving the SSP’s, as it is understood that different approaches are being taken by several Flag States. For example, The MI is one of the registered IACS members which own the responsibility to act as RSO for the approval of SSPs on its own behalf.
Flag States delimits the needs for a Security declaration. DOS usually refers to the security during vessel facility and vessel interface. The DoS is a strong medium which is exclusively designed to ensure critical security issues prior to and during a vessel/facility interface.
The SSP and the PFSP work combine and they do not take preference over each other. The DoS is traditionally used to identify several responsibilities and main concerns which includes port facility and the ship (International Transport Workers’ Federation.2009: 3). The main objective of the DoS is to make sure the ship and the port would not be 2 different entities that do not communicate with each other but rather 2 different entities which combine to make a whole structure which is usually greater than the sum of the parts.
“The performance of a flag being used by a fully compliant shipping company may. Impinge directly on that company’s performance. Ships flying a flag whose vessels have Shown higher than average levels of non-compliance during port state control inspections are generally subject to special port state control targeting and thus greater numbers of inspections. For the compliant operator this can mean unnecessary delays, plus greater potential for charterers’ penalties. Moreover, on ships using flag with a poorer record, port state control inspectors may be more inclined to make an issue of routine non-critical deficiencies caused by genuine ‘wear and tear’ during the preceding voyage.” (Maritime International Services)
Flag States will certify a defined Synopsis Record CSR, which contains a birth to death history and also highlights all changes takes place regarding the ownership of the vessel during its whole life (United Nations 2007: 1).
CSR is basically a record which gives a birth to death history including all major and minor changes regarding to the land lordship of the vases. Flag States are also highly responsible for evaluating the various security threats across the world and after evaluating its biggest responsibility of flag states apply all security levels as appropriate. Flag States will give a security advice to ship-owners regarding vessel security and it should be of level 3 and 24/7 hours service.
In other words, Flag States hold a responsibility to assist owners by understanding the basic requirements that what is actually required under the ISPS Code. Following are some basic needs and requirements which every owner wants to be considered for effective output.
- Security Awareness.
- Cooperation.
- Communication.
- Training.
The ISPS Code is developed by keeping an eye on a similar framework of the ISM Code and the processes for review and implementation. After the 9/11 terrorist attacks on the USA in 2001 security has become the most important concern in recent world. The effects of terrorism were really high due to which numerous things have been reformed now in order to take preventive measures against terrorist attacks (Flag State Control, 2009: 1).
After these attacks shipping has also faced different challenges and it has also suffered by the terrorists, like the USS Cole and the Tanker Limburg. There are several possible terrorist threats which hold shipping involvements; few of them are listed below:
- Ships can be used to send weapons from one location to another for terrorism.
- Ships or containers filled with chemicals can be used for any terrorism activity at posts or busy shopping lanes.
- Ships themselves can be a victim of terrorist attacks same as USS Cole and Limburg.
- Piracy over the last few decades, security measures at airport is become sensitive at such places where vessels are the dangerous targets. At such places, flags play a pivotal role and help a lot in preventing such terrorist attacks.
Beside flag registry there are several other factors which need to be considered and those factors can provide security up to some extent. Sometimes, these codes get fail in certain situations. The ISPS code is renowned technique for security of vessels. Sometimes, ISPS code does not work as there are undoubtedly various reasons which answers that why it is usually difficult to deploy the ISPS Code in vessels, reversely there are a number of reasons which answers why it should be deployed effectively (Regulatory Framework 2009: 1).
For the success of ISPS code, several factors needs consideration and each part must perform its own responsibility. Following is the brief discussion about individual’s responsibility.
The Ship and its owners
Both, ship and its owner need to perform a heavy role on the path of success. Now the question arises what is the main responsibility of staff and owner?
The ISPS Code gives a complete pattern, for the improvement in communication and co-operation in order to achieve effective output in less time. A framework is exclusively design keeping an eye on changing needs and requirements which should improve communication and co-operation on the ship board and at all places on the ship. All organization must hire security officers for keeping the check on various activities taking place on ship. The Security Officer holds a detailed duty list which includes 13 items. For effective implementation and success of ISPs codes it’s really important to fulfil those responsibilities. Now the question arises do these duties actually work. Generally, it is the security officers’ duty to create a culture in which every one can communicate and participate freely.
A culture should be designed in such a way to prevent every negative feeling among the staff of the fleet. Security officer role is very important in overall process. His role is quiet similar as the DPA under ISM whose primary responsibility is to raise the safety cognizance of the ship’s crew and the management. Security officer job is really tough as he has to face lot of challenges and he requires performing a strong role in order to implement high security measures. The SSO’s job could be concluded as developing a culture and security environment on ship board through training, workshops, seminars and exercises, like safety drills.
Its primary responsibility is to create a healthy environment between staff members as healthy and free environment can help in reducing crime rate and negative feelings. There should be a great communication path between the ship’s staff, security officers and the management in order to make sure that every single member is completely involve in each step. In several cases the success of pirate terrorist attacks on Vessels usually highlights that the piracy procedure did not implemented effectively. The advantage of awareness brings lots of advantages in implementing effective measures specifically ISPS Code.
Coastal States and Port Facilities
Beside, ship and its owner other elements should also perform their responsibilities honestly. Under the Code the Coastal State and Port Facilities also poses some responsibilities within that state.
These responsibilities also need to be fulfilled accordingly the specific rules and standards.
Moreover, Port States will investigate ships to assess the effectiveness of SSP and posses the power to delay vessels if required, in approximately the same way as the ISM Code is retrieved.
Why Registry role is important?
“The shipping company, and not least its charterers, may also have general concerns about the Implications for its corporate reputation of being associated with a poorly performing flag, even if the company’s ships are fully compliant.” (Barrister H. R. 2008: 1).
Registry role has become significantly important as now people are more aware and they need each and everything perfect and on time. When they pay high wages for owning a ship trip or for transferring their loads they do not compromise at any stage. They ask for the best and want to be treated first class. For that, several things needs consideration, among all flag registry is one of the most important which need special attention for effective and desired results.
Owners usually set criteria first while choosing flag registry. Owners usually follow some guidelines for the selection of registry flag. Every individual want unique design that neither any other party is using that nor it will use that. Every individual wants the best and unique registry for his ship or crew. Beside design every one wants the best security techniques applied at his place so that he can make sure all members regarding safety and security issues. For the effective implementation, company usually hire a security officer whose primary responsibility is to take care and review each step involved in security implementation at place. Its primary responsibility is to create such environment in which staff and management can communicate easily.
Factors governing choice of flag
The Choice of flag is an ownership of the ship-owner. It is to decide where to flag the vessel of his ship. There should be important choice between registering a vessel in a country (Manahanm D.T, 1990: 1). The person or a company who is owning the choice of flag should have real connection by way of economic and national ties and an entering in registering which will accept the vessel irrespective of the nationality of the persons beneficially being super active and take keen interest in the vessel or the country from which the vessel is actively controlled.
Moreover, the company may seek to rejoice certain of the benefits for an open registry system for retaining maritime links of tradition supported by entering the vessel in a secondary registry one (1) by the function of the bareboat charter registration in the other country. The impact on the factors of choice will be economic and political. The flag state defined by the law of the Sea under United Nations Convention (UNCLOS). With the reference of the book Stopford 1997, pg 431 which states the choice of register has become a major issue for ship owners. The reason is the interdependence between legal regulation and ship operating economic issues. These factors are important for them. Ship owners can also take benefit of this. They can be in the position that they can choose the countries to register their ships.
Concepts of Registry
A flag of convenience is ship where the nationality of the owner belongs to different region from the country of registration. The concept behind the registry can infer the meanings of registration of the ship, batch and the customers of the ship-owners. The idea is to focus on the services of the customers for ship-owner who know the need for strong and long lasting Maritime administration. A Maritime administration is to create fully equipped tools to follow the standards of International Treaties, Laws and Regulations to uphold the ship-owners to enhance and expenditure their business in a tough International marketplace (EFFECTIVE FLAG STATE CONTROL 2009: 1).
When concept of registry was introduced then only those countries which were influenced by United States of America registered their ships and opened those registers for general public. In that era only few countries have registered their ships. The most famous registries at that time were Panamanian, Liberian and Honduran and some other countries as well. They introduced open registers. Those countries are Panama, Liberia, Marshall Islands, Bahamas, Malta, Cyprus, Antigua & Barbuda, Saint Vincent, Bermuda and Cayman Island. The total world fleet tonnage is 585.9 mill dwt (more than ships of 300gt).
Panama’s share is 23.2% of world fleet of 250 mill dwt. whereas; Liberia’s share is 10.7% of 115 mill dwt. Both countries shares increased to 7.3% in 2004 and 2005. Marshall Island’s share is more than both former countries. Her share grows 20.1% per year. Figure five analysis shows increasing concentration in use of foreign flags among ship owners in 1995 and 2008. In 1995, index was 100. In 2008 it increased to 212. On the other hand, use of national flags decreased in 1995 and 2002. From 2002 use of national flags increased from 85 to 105 in 2008. Ship owners prefer to register in countries where they have no national connection.
On 1st of January, 2008 691 mill dwt was equal to 65% of total merchant fleet tonnage. These ships were registered under foreign flags. These were open registries.
According to Institute of Shipping Economics and Logistics, 2008 Lord Rochdale explained maritime business with certain features of states of registers.
- Country with open register allows non nationals.
- Access is easy.
- Taxes are levied paid on ship income not to be paid locally.
- Register country does not possess any national requirement connected to registry.
- Non nationals are allowed to use or sail ships.
- Register country does not have to do anything with rules and international regulations.
Lord Rochdale accomplished an investigation in 1967 and 1970.
The purpose of this investigation was to analyze the United Kingdom shipping industry. In that era the industry was characterized by seafarers strikes. Lord Rochdale also observed international industry. He noticed the areas in which those industries were effective, efficient and competitive. In order to do this he looked at Linear Conference and tried to find out the reason that why ships were flagged out from UK to Flag of Convenience.
Following is the list of flag of convenience: Bahamas, The Antigua and Barbuda, Barbados, Bahrain, Belize, Cape Verde, Comoros, Liberia, Cyprus, East Timor, Equatorial Guinea, Faroe Islands, Bolivia, Georgia, Jamaica, Gambia, Netherlands Antilles, Korea, North Honduras ,Liechtenstein, Lebanon, Luxembourg, Marshall Islands, Mongolia, Malta, Monaco, Mauritius, Kuwait.
UK Dependencies
Following are UK dependencies
Cayman Islands, Ascension Island, Gibraltar, Falklands, Bermuda, Guernsey, Isle of Man, Jersey.
Open Registers
It can be described as the benefits to the open registry state and the ship-owner. Two other influences of the open registers are 1- the political will of the States to comply with the International requirements and the other for those which are not influence by such a will (Voluntary IMO scheme 2008: 1). The state maintains that include open registers include vessels whether is state owned or franchised out to commercial entity. Open registry systems are the benefits they bring to the flag state. Economic benefits could be realized as follows:
- registration fees and tonnage taxes;
- royalty fee and or franchise;
- outsourcing due to reduced government expense.
Although less significant benefits may be sourced from the revenue generating from incorporation, taxes of all kinds and other fee associated with different level of residencies of the country. The use of open registers for ship-owners is both legal and economic. Open registers benefits to the ship-owners as follows:
- no vessel restrictions or is low;
- Suitable tax environment.
- administration and registration fees are nominal;
- operational costs of the vessel is lower.
Economic
The purpose of the Economic is to set out the commitment by the government of the Maritime areas and Providence adjacent to economic cooperation with the aim of getting economic self-reliance for the Maritime Provinces and thereby improving the well-being and prosperity of the people residing in the Maritime Provinces.
Tax, company law and financial law
Tax: applies to the workers salary. It covers the law of the country being followed by their employers and every employee has to abide by the tax law of the maritime of the same country and other country.
Company Law
The Company law covers a full range of commercial and corporate legal issues to businesses of all nature. Entrepreneurs, companies of national prestige and multinationals clients include corporate clients of foreign.
Financial Law
This deals with the big range of the savings and investments, products where individuals have business, organizations and institutions there they hold billion and trillion of investment against the services they render. This financial investment for maritime holds the level of high standards of the world class economy (Young, E. 2005, 1). This helps ensure the company to buy new stuff and for improving critical and service areas where finance is needed.
Aims
Since 2001, terrorist attacks all ship owners are more alert and interested in owning strict effective measures in order to protect the vessels. As ship industry is facing a lot of challenges regarding to vessels safety. A ship owner usually wants to have the best at economical rates. Following are few points which are considered as the criteria for a ship owner for choosing flag registry (International Transport Workers’ Federation, 2008: 1). The design must be unique and ideal across the world at least in that region No other organization is using the same design or variations with colours, he always needs the unique and different design for its vessel (Stopford, 1997:1).
The design must be in simple form so that any one can easily understand and it should be a public domain, public domain is not subjected to copyright. County flags should be designed in such a way to present each and every aspect and the flags can be normally applied to a historical county instead of modern administrative area
The flag must own one of the following
- It should be registered from the College of Arms;
- It should be registered with the Office of the Lord Lyon;
- It should be selected by public vote.
Objectives
Security
Security is one of the most important issues in recent days. Terrorism has become one of the biggest threat for which all ship owners are interested in implementing new and advance technologies (The national Union of Seamen of Great Britan. (1981: 1). New and advance technologies help a lot in keeping safe the environment, ships and crews. Registry and flag state play a pivotal role in creating safe environment on ships and crews.
Flag registry gives a clear picture that how security measures should be implemented and who are responsible in implementing effective security measures. There is a strong need that every one involved in this process should perform his duties honestly. The security officer is highly responsible for developing such environment which creates a free communication bridge between staff member sand the management. Clear and concise communication between staff members helps a lot in implementing strong effective measures.
Summary of proposed methodology
Internet
This world has become a global village now and internet is considered as a biggest source of information in this world. Internet is a biggest source of information which helps in finding required material on few clicks. When a ship owner wants flag of convenience he can find all related information on internet in few moments. Internet has all things related to ship and flag registry worldwide. An owner can also find best criteria and sources of getting flag register. Internet provides updated information as they get updated on weekly or daily basis. The basic advantage of internet sites is that they contain every thing relevant and the information is selective (Coles, R. 2002: 1).
A person does not have to wait for long to find his required news and content. He can open any site and read its required content within seconds. There is no need to wait for long or to waste time in searching required material. Several searching engines help in this vein. By using searching engines one can easily find all facts and figures about flag of convenience and its cost measures. Internet and several website also offer online communication and feedback facility 24 hours. One can simply login and raise a query about shipment and flag registry and he will get a reply within few minutes. This is the only reason why thousands of users want to search internet instead of going through books.
All information used in this paper is collected from internet and books. Most of the information is collected from websites and online material. All about shipping industry one can easily find on internet as internet has become one of the largest source of information worldwide. On internet an owner can find out the main reasons why ship owners needs to get flag registry but unfortunately none of the web sites give complete details about registry and flag states. The biggest advantage of internet websites is that they get updated on hourly, weekly and monthly basis. One can also find the recent reports and surveys on flag registers and flag of convenience.
Globalization has now affected business community and businesses to great extent. Political, geographical, and businesses environments all over the world has come closer to each other. Implementation of computer technology, networks and media has made information and worldwide news assessable for everyone. Nations are now aware of different cultures, religion, politics, and businesses of other countries. Decisions taken in one part of the world will have its effects and responses in the next part of the world. This way, the whole business community around the world has not only become interconnected with other but is now dependent on each other.
Networks are formed to share information, communicate, share single hardware devices like printers, scanners, etc. Businesses and organizations exchange their work, information, with online payments systems. Internet offers all businesses, social, and commercial operations in a fast shortest possible time at very reduced cost. Network of worldwide users has changed the way businesses our done today.
It has increased profitability and reduced time period in which businesses, commerce and trade are accomplished. This is due to the tremendous exposure of businesses on the net with worldwide users. In this way to compete today’s market and to fully access growing advantages, organizations and companies need to implement network (intranet & internet) in their core technology.
Significance of secure networks
As with so much opportunity on the Internet one cannot deny great benefits it provides to its users. However, there are certain security risks, which are inherent to the Internet. But one cannot remain isolate or keep their business away from this big opportunity due to the threats on the networks.
There is a need to secure networks to protect it from being in the hands of illegitimate users or even legitimate users who are not allowed to assess private information. Network security will protect loss of any private, secret information exchanged between authorized users from unauthorized users. Information may include any type of data saved on hard disks of interconnected computers, on web servers, transmission over the Internet like email messaging, financial and business information.
Security also implies to the protection of systems on which data is saved. This includes protecting computers, networking elements, services and applications.
Protecting networks is important for keeping the information confidential, to maintain the integrity of information, authentication of legalize users, and availability of data.
Possible threats and dangers to the Networks
A threat to the secure data on computers comes from both inside and outside users. It may be intended or it may be unintentional and accidental. There are also passive and active threats. Passive threats are those where only secure information is released without affecting the system (Computer Security, 1998). In case of active threats, information and system both are affected (Computer Security, 1998) and this is mostly intentional.
Threats could be from hackers who masquerade for accessing secure data or spreading virus. Insider attacks could come from the loss of confidential secure data by authorized users where as outsider attacks are intentional site invasion or data access by illegitimate users. Creation of trap doors that allow unauthorized person to access information. Virus attacks that may damage important data, files and hardware. Exhaustion attacks to access passwords or any other encrypt data. Other accidental failures including hazards to equipment and systems. For e.g., power failures, rain/snow/air storm, earthquakes etc.
A description of the major transactions within the website
Protection from outside threat
Protection from external threats include implications of following measures:
Encryption Software/data
Encryption is to encode the information into an unreadable format using specific mathematical key. In this way message cannot be read in the hands of unauthorized persons. Only authorized person having the same matching key can decrypt and read the message.
There are different encryption models for encrypting/decrypting files. These models in turn have variable keys, coming in various size and numbers. The smaller the key, the easier is to crack the message. Therefore, for very secure and confidential information, larger and tougher keys should be used to encode and decode the messages.
Two types of keys are important for encryption system i.e., single key and public/private key. In case of single key there is only one key which is exchanged by the companies privately and which is not known by any third party or unauthorized users. Where as public/private key is a pair of public and private key. Public key is known to public and anyone can use that key to send encrypted messages to the company. While private key is only known by the company to send encrypted messages and to verify digital signatures.
There is a system called Public key infrastructure operated by certifying authorities to provide key management. It is a secure management of encryption key to give access to only those users who are authorized and should be available to them only when it is needed.
In addition there are Data Encryption Standard (DES) and Advanced Encryption Standard (AES) which are widely used for data encryption. These encryption methods use private key, which could have trillions or quadrillions possible keys. For sending and reviewing the message same key should be applied on both sides.
Virus Scanners
Checking for any new viruses and worms is mandatory like Trojan horse. Companies should have technical staff and virus scanners updated to prevent any new virus intervene into the network.
Remote access
All users should be limited to access only those areas of network where they have their job to be done. Shared accounts should be avoided. Monitoring of account activity is also necessary. Implementation of authentic system into such remote areas is mandatory. There should be proper log off and log on systems using passwords. All users should be abiding by user agreement.
Implementation of passwords
Passwords are very useful in restricting access to any type of data. Implementation of passwords to the system should be properly done by technical and well-trained staff.
Installation of firewalls
Firewalls are the most important way of controlling flow of information on Internet and providing sound security. This security mechanism is called metaphorically as firewall as its work is same as physical firewall. It stands as a barrier and protects the network and access to the information from malicious attacks (fire). Firewall may be software or hardware that filters the incoming messages and keeps away dangerous messages like messages containing viruses or decryption codes (Tyson). Any information flowing from Internet to private network is controlled. Its installation needs expert assistance.
If large numbers of computers are connected together with one or more connection lines to the Internet without the placement of the firewalls any computer will have access to the data on any other computer on the net through FTP, telnet etc. However, if a firewall is installed correctly at each Internet connection it will permit and block traffic only to limited number of computers. By setting up rules for Web servers, Telnet and FTP servers the company can control employees access to the websites, local networks, information retrieval and loss.
There are different methods of using firewalls; they may be Network level firewalls (also called packet filtering), application level firewall (proxy service) and stateful inspection/filtering method for securing inflow and outflow of traffic from network. In case of packet filtering (network level firewalls) routers form connections at various levels of network. It involves filtering of packets, which are small pieces of data, and then sending it to the requesting system. However, routers cannot perform complex functions. In case of proxy server (application level firewalls) information retrieved from and sent to the Internet is checked.
It provides high level of security. Stateful inspection is the method in which individual packets are analyzed for sensitive data within the packet, which is then compared with other reliable database rules and information. In addition, characteristics of out-flowing and in-flowing information are also compared to be permitted through the network or rejected.
Books
Books and journals play an important role and there are thousands of online journals which cover the topic and give detailed knowledge on a topic and there are several books that covers the subject of different types of flags a ship owner can use those books and journals for easy guide and authentic information. Numerous books have detailed content about each and every stage of the flag registry many books illustrates answers of various questions comes in mind of ship owner while getting flag registry Many of these books are up to date as authors usually revised editions of their books. Unfortunately there are only few journals available online that covers the subject.
Therefore it is little difficult to find any beneficial information online. Lots of information is available online and in books and people usually go for those resources which are easy to access and readable. Major information on this topic can be available from internet websites and from books as there are very few online journals available for free access. When a ship owner wants to get a flag registry for the security of his ship he first searches those resources which contain easy and readable data. A ship owner usually goes for search engines first in order to find out its required information. One will find books covering the topic in libraries and in a book shop.
Increasing Use of online libraries as source of information
There is no debate that libaries are very important sources of information especially for academics and scholarly audience. In today’s globalization and technology era, where diseases are spreading without boundaries, and in places where there is shortage of health care services, online libraries play important role not only for the academic and scholarly audience but also for the non-scholarly audience.
With the extensive use of computer technology, online libraries gives people around the world equal access to similar information and it benefits both the libraries and users.
On page one of his abstract, Vrana says, “The advent of digital information resources changed library organization and management intensely.”
The initial changes from printed form to digital form is in the conjuction with the growth of online higher learning even in medical specialization. If online higher learning institutions cannot provide prompt and adequate access to digital format, students would be in trouble so is the credential of the institution. Consequently, the quantity of digital format information is increasing, so are the automated and digital libraries. Commercial publishers as well are trying to enhance their existing services by developing online access services to meet the increasing needs of their users for full text scholarly and non-scholarly information.
Since the demand of the users for both scholarly and non-scholarly information in digital format are increasing, libraries are increasing their collection of digital information to meet this demand. Nonprofit organizations as well are providing services for online libraries that contain health information.
Journals represent scholarly communication can be easily available to people around the world at an instant access. They come in different forms such as data table, multi media, or other part of information that is not included in the printed form.
Seeing the change in the way consumers’ need for information and the sophisticated technology and its usage, libraries find that online provision needs to be expanded a long with the growing service of online higher learning. As digital format information is growing in its importance, so is its acceptance among the academics and scholars. Michaelson & Garret find that even America Physical Society declares that online journals are just as official as the printed journal. This indicates that the content of online libraries are credible source of information on health issue.
Some of the benefits of online libraries are, according to Michaelson and Garret, cheaper cost compare to the printed form in terms of binding and storing; convenient access for the users because they can access the information from anywhere around the world and at any time possible.
Different from the traditional libraries, there is no potential that the information is not available because it is rented out. The information is also searchable and people can searh for the information more effectively without reading through all the pages.
The McNeese State University describes that the advantages of online libraries are its standard classification system which makes the information to be easily located; the quality of material is purchased based on selection criteria; and the information available are in historial format.
Another advantage of online libraries may also include the simplicity of cataloguing and classification system, which are a little different from that of the traditional system. The traditional cataloguing and classification are without links which tend to add to research time, while online libraries, if properly designed, may offer links that make users’ research time is more efficient. In addition, modern automated libraries, says Vrana, transform “their card catalogues first into online public access catalogues (OPACs), and then to Web public access catalogues (WebPACCs) offering means of information discovery by giving access to bibliographic records about information resources, which are part of library holdings.”
Moreover, online libraries provide digital links to different sites that are related to the state information with search and retrieval tools that make it easy for the users to obtain the information at a click of the mouse. If the links are designed in such a way that would cover a global grid, the opportunity for the users to increase their knowledge in terms of qualitative research globally also increase.
For the above advantages, universities in Western Europe, North America, and Japan have offered the delivery of their courses material in digitalized format including courses in health care.
Online libraries do have some disadvantages, though. For example, the information acquired is based on planned acquisitions. Reynolds & Wilson describe that, though not exactly accurate, online materials compiled are often less up-to-date, for the historical data, they tend to have no explanatory notes, and no apparatus criticus.
The McNeese State University describes that the disadvantages of online libraries are that not all information are available because others, especially the important ones are available only in printed form. Similarly, digital format is not as complete as traditional format unless the online libraries are willing to extend their service to produce online information in the book format where users have access to complete information. Vrana also indicates that the problem in some online libraries is that they do not have “dynamic links between bibliographic records and information” associated with the references they are giving.
Unfortunately, says Vrana, digital libraries are still outnumbered by automated libraries because automated libraries are offering more diverse and aggregate information to both commercial and non-commercial audience, particularly to academic community.
In addition, online libraries open all the time and the material borrowed is not returnable or that users would not be penalized for late return. Since digital libraries are growing in demand for its services and content, and whose services are very important to academic and scientific worlds, Vrana suggests that it is important for online libraries to extend its contents by providing additional services such as direct linkage to citation or reference to the information in the form of full text stored in the database of either the library or in the database of different library.
Data collection
Questionnaires were developed for officials and staff and their relative data and progression will be obtained from the concerned flag ships offices.
First priority would be to select a number of flag ships. Then from that data obtaining the list of current officials and those officials who recently left. Then we will obtain contact information of those officials.
Our first option would be to contact through phone and have an interview date fixed if the officials agree to meet and fill out the questionnaire. Those officials with whom contact on phone is not possible will be contact through a mail typed letter. All letters and questionnaires and letter will be typed in Times New Roman 12 pt. Officials who will not have time for a meeting but they agree to fill out questionnaires will be mailed those questions. Emails and surveys through Internet is also possible. A survey form will be uploaded on a website and various flag ship websites will be contacted for information list of VAP officials. Individuals can also be contacted on forums, email groups for those who have been VAP officials. Officials’ will be passed a URL for a questionnaire and will asked to fill it with sincerity and honesty.
Officials currently will be offered survey at their ship. Their progression will be obtained from the ship staff.
Subjects will be divided into those who were
- Only Interviewed.
- Only Filled Questionnaires.
- Both gave interview and also filled surveys.
There are several methods to contact officials:
- Direct contact (for e.g., those in neighbors, family, ship officials)
- By Phone: If phone number will be available through data or other contact then first preference would be to contact on phone and get a time for interview and questionnaires. If the officials opt for giving a phone interview and fill questionnaire on phone that will also be accepted. A written consent will be made on his/her behalf.
- By mail: Those subjects with whom we are unable to contact on phone will be mailed typed letters. In letters we will provide our complete contact information including phone numbers, mobile numbers and emails and online survey forms. If we will get response from them then they will be contacted either by phone (if provided by them) or we will send them forms and questionnaires by mail.
- Online Forms/Questionnaires: We will also tell them our website URL where forms and questionnaires are uploaded. If they have this facility of computer then they can fill it out on the Internet.
Most of the survey questions are same as used by previous researches; Grap (2003) used survey questions. Every question was followed by space to write their comments.
How to use the data
Data should be used in an approtiate way so that each and every instance would be clear Summary data with different aspects of flag state performance, retrieved from information available on different resources especially in the public domain is used effectively in order to produce effective output. Www.marisec.org/flag-performance table on website is updated daily and it contains updated information for practical use and implementation. Like all other statistics, the data collected should be handled with care. A single instance will provide an unauthentic measurement of performance. However, when there are a huge variety of indicators the choice becomes easy and a number of indicators suggest that a flag can bear unsatisfactory performance.
Primary
A researcher stands highly responsible for the matter under his investigation. He’s responsible for all his actions from researching to writing, and he must be honest in his research and written words.
Research itself must follow highest standards of integrity. A research needs to solve a problem in an effective and reliable way to produce “valid” results. The overall research work depends on its experimental design, analysis of relative data generated from the research, interpretation of analyzed data, conclusions & discussion, using primary and secondary sources for writing literature, and acknowledging all the contributions from direct and indirect sources correctly is the real essence of a good research. A good research piece comprises first intensively researching all possible and reliable sources to conduct research and then using most recent and reliable literature to interpret the results.
A good research piece has following key elements
- It is most intensive and thorough.
- Follows high standards of integrity.
- It must comply with all recognized international standards of research.
- Methodology & logic must be free from any flaws that might produce errors in the results.
- It is documented in a well-written, readable, understandable, well-formatted paper proving researcher’s point clearly with validated sources.
- Clear conclusions must be drawn to prove the thesis and pose new issues.
This applies that researcher should have enough funds from reliable sources to conduct his/her research successfully.
This applies to the whole range of research work, including experimental design, generating and analyzing data, applying for funding, publishing results, and acknowledging the direct and indirect contribution of colleagues, collaborators and others.
Sound research is the basis of every form of factual writing and some forms of fiction. Aside from the obvious avoidance of plagiarism and fabrication, there are important rules that must be followed.
Sources are the essence of research and the best source in research is a primary one such as a direct interview or handling of the research material. Typically, though, only secondary research is available. In such a case, it is important to use several complimentary sources. Sources should be documented accurately, completely and be verifiable by the reader.
Bias should absolutely be avoided in research. The sources should state facts without any obvious bias and the writer of the work should follow suit. In line with avoiding bias, the writer should also avoid generalizations. It is rare to find a true “always” or “never” in any type of research so they should be completely avoided in writing.
A research writer is comprised of two major aspects, an excellent researcher and an excellent writer. An excellent researcher keeps the subject matter unbiased, balanced and focused. An excellent writer adheres, unwavering, to the subject matter and makes use of proper grammar and usage rules.
A scientific researcher is a qualified research writer because he fully researches all subject matter prior to beginning any written work and strives to produce a balanced document regardless of the topic. He is unique from many writers in that he enjoys research as a learning tool rather than a skill I have simply mastered.
Research methodology
For the methodology must include some statistical tests to illustrate the quantitative difference in performance.
This may include econometric techniques such as regressions, correlations, OLS, residual standard error, multiple R-Square, adjusted R-squared, F-statistic and p-value being used were possible.
The NAV should be used were possible as an indicator of performance. DataStream would be the preferred statistical package if possible as it was used throughout the masters programmed.
Different statistics operation must be used to analyze the data. Pearson correlation is to be used to evaluate interrelations and Pearson Chi-Square was used to evaluate predictive frequencies and odds ratios. Frequency distribution is used to evaluate frequency of a (value) occurring in a data file to describe the data distribution. The data is of nominal level.
The frequency distribution table is constructed to organize the data to list all the variables in a column and the frequency of occurrence (count) against it in another column. For calculating purpose, frequency is the number of times the value appears and it is written against those values, which have zero frequency for calculating frequency polygons.
Secondary
Statistical Analysis
Probability is “A value between zero and one, inclusive, describing the relative possibility (chance or likelihood) an event will occur.”
It can be computed as
![]()
Classical probability states that “A probability based on the assumption that outcomes of an experiment are equally likely.” It can be calculated with the number of favorable outcomes divided by the total number of possible outcomes.
Empirical probability depends on the past experiences and observations. On the basis of past observations, one can compute or judge the future outcomes.
Subjective probability depends on personal judgments instead of computations.
Classical
It can be computed as
![]()
Empirical
“Occurs when the number of times an event happens is divided by the total number of observations.” (Lincoln)
![]()
Subjective
“The likelihood (probability) of a particular event happening that is assigned by an individual based on whatever information is available.” (Lincoln)
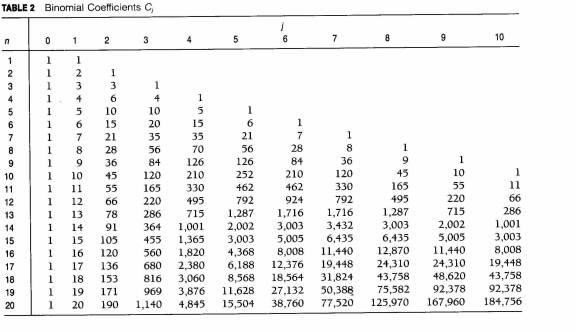
Binomial distribution
P {j successes and n-j failures} = Cj pj(1-p)n-j
Cj = binomial coefficient. It is an integer and is a function of j (and also of n)
Bionomial coefficients are shown in statistical tables or can be found by binomial expansion
Calculating binomial probabilities if p = 0.39 and n = 5.
Poisson formula
P(X) = e–mmx/X! or P(X) = mx/ emX!
The computational formula often used to evaluate probability is
P(X) = P(X-1)m/X
Where,
- P(X) = the probability of X occurrences
- m = the population mean of occurrences.
Example (from Zar 1996): It is expected that 52 purchases will be made by each consumer and total number of purchases on which they will be the expected to deliver one price may be 19.23.
n=52 [average purchases per year]
m= 1000 [total purchases] /52 purchases = 19.23.
Measure of Central Tendency
The central tendency is measured to summarize the data obtained into single parameter using mean, median and mode. It determines the central core value of data distributed. All numbers are written in the series and their central value is calculated.
The mean value is calculated by summing up all the values divided by the number of observations in all the data set. Mean value can be expressed as mean (x ̅) =Σ(Xi)/N (4+7/2)
Xi = the individual values,
N = number of values, and
Sigma (Σ) = sign of summation.
Mode is determined for the series of data. The value with greatest frequency is the mode. That is, the value that appears many times in a data set is mode. In a set of number for e.g, [3 4 4 5 6 8 9] 4 is mode.
Median is the middle value when the data is organized in ascending order. It may be the average of the two middle values [if two different values are in the middle]. In a set of samples (numbers), for example, [3,4,4,6,8,9], average of 4+6/2=5 is median.
Measure of dispersion
Measures of dispersion is also calculated because measure of central tendency does not calculate the dispersion of the test within the data set.
Range
Range will be calculated, which is the distance between the peak and the lowest value. Range, variance and standard deviation are calculated as a measure of dispersion.
After estimating range of higher and lower values, standard deviation will be calculated.
Range is the simplest way of measuring dispersion. Range is the difference of peak value and the smallest value. The lowest value is subtracted from the peak value to find out range. Because mean is the calculated by the average of all values, range shows the variability in the set of data when shown against mean.
The range, variance and standard deviation of data collected for RNs will be calculated and shown in separate table.
The range of the data set is estimated by subtracting (smallest value in the data set =4) from the largest value (=7).
Range = Peak value – smallest value [7-4=3]
Variance and Standard Deviation (SD)
Because range does not provide the estimation of how the data is dispersed around mean therefore standard deviation (SD) is also calculated.
Variance is obtained by calculating deviations of original values (Xi) from the mean (x). The variance (S2) is calculated by S2 = (Xi -x ̅) [Σ(2] /(N-1)Σ= summation sign
Deviation of original values from mean = (Xi -)2N = number of observations Xi = $10 ($10-x ̅)
Standard deviation (S) is calculated by deriving the square root of the variance (√S2 )
For example, If S2 = 1000 / 10
S = 10
SD = ![]()
Confidence level = 98%.
SD = $500.
Per sample = $5.
Total sampling cost = $10,000.
Number of sample = 2000.
Standard deviation provides the important evaluation of the distribution of data about the mean value. If one standard deviation is subtracted or added in mean will give 68% of the dimensions of the data series. If two standard deviations are subtracted or added in the mean then it will give 95% of the dimensions in the data series.
- 68% = mean + one standard deviation
- 95% = mean + two standard deviation
It is a fact that even the most novel and new research requires a lot of support from the previous work done in that area or in related areas. The research builds its self upon the beams of prior researches. Its steps forward on the foundations of the past effort done, and move towards the conclusion. Thus help from other researchers or experts in related fields is a part of almost any research. One way of getting this help is though personal conversations or more formally-interviews. These interviews are considered the primary source of information, with documents being the second.
A person, who is considered worth an expert in the field of the current research, is interviewed for his opinions and thoughts about the research. Hence, this interview(s) play very crucial part in paving a way to wards the conclusion; in some cases an interview might cause a research to take a U-turn in terms of conclusions. Therefore, the authenticity and reliability of the interviews conducted for research should not be ignored. Particularly, when the research is related to health care i.e. lives are depending on the conclusion of the research then, the authenticity and reliability of the interviews are of absolute significance.
Unfortunately, for the researcher the burden of judging the credibility of an interview is upon his shoulders. And there are basically two ways he can cop with this problem, first method needs the researcher himself to critically analyze the interview authenticity. This procedure of critical analysis sometimes might not prove very beneficial, because sometimes the interview might fully support the researchers own idea, in which case the researcher is very likely to be biased towards himself, and in doing so he might announce all the interview output to be correct with out going into the process of any verification.
The second method is a little more reliable at its core; this involves double checking the points concluded in an interview, by either concerning another related expert in that field and asking him the same questions again or by giving him the output of the interview and asking him his comments. Although, this method is a little more reliable than the first one however, it too has a problem associated with it. The problem is that the second person who is considered for double checking might not be ready to take the pain of a serious review and he might say a straight ‘YES’ to all your conclusions without verifying them appropriately.
So the authenticity and reliability are serious issues attached with any interview conducted for helping a researcher in his research, especially they pose a greater threat when the research is in the area of health care.. These problems though can be lessened by the two methods suggested but they surely can not be eliminated fully.
A researcher must be honest, sincere, truthful, dedicated, and aimed at to learn more with his research study.
Conclusion
The debate on these issues has done at various levels but it must be implemented for effective outcomes. Not only it is must be deployed but it should be strongly implemented, if PSC wants clear grounds to distrust a vessel is not abiding by the ISPS Code the vessel can be delayed, or it may get refusal at any place. In some situations, The ISM Code doesn’t work and neither the ISPS Code works effectively!
Number of researches proved that ISM codes are not 100% perfect and it should not be implemented. But, in certain cases where companies have a serious and strong approach towards safety and security from the top management till the down management it can work if properly implemented. Companies when deploy the ISPS Code effectively they gain advantage of it too. Some analyst suggests that these codes work better in Tankers however there are also some conditions.
Those organization which are non serious in expanding high efforts in order to take safety measures and to expand eventually fall in great trouble and faces security laps at several places. If such organizations spent many efforts in the implementation of ISM then they will always be on safe side and ISPS an ISM code will work fine for them.
The success of these codes is all depends on the setup and its management. Both ISPS and ISM codes are effective but they are dependant of strong implementation and efforts. In other words, security does not want a single specified line of work; it varies with the passage of time. In order to meet standards both codes implementations should be reviewed in short intervals. The SSP is not cast in stone; it is only a document which needs to be changed with respect of time.
Implementing security measures is a team effort which decides the success and failure of the ISPS Code. For proper and effective implementation of ISPS codes all industries particularly the Shipping Industry, the Port Industry and the Coastal State will need to work with mutual understanding than before and the several parts of the each industry will have to work more closely altogether (Barrister H. R. 2008: 1).
This is obviously not a game to be happening overnight, it needs time and efforts from all four sides. It could be developed by mutual sharing and understanding.
List of References
Flag State Performance, (2006). Shipping Industry Guidelines, Maritime International Secretariat Services Limited.
The Role of the Flag State in Ship Finance, (2009). Web.
Ship Mortgages as a Financing Vehicle: The Flag State’s Role in Protecting the Security Interests of Lenders, (2009). Web.
Shipping Industry Guidelines on Flag State Performance”, (2006). Maritime International Secretariat Services Limited. Web.
Toweh, (2008). “Shipping’s flag of convenience pays off for Liberia”. Business Day. Web.
International Transport Workers’ Federation. “FOC Countries”, (2009). Web.
Carlisle, Rodney (1981). Sovereignty. Web.
Vessel Registration and Mortgage Recordation Procedures, (2009). Web.
International Transport Workers’ Federation. (2009). “What are Flags of Convenience?”. Web.
United Nations (2007). “United Nations Convention on Conditions for Registration of Ships”. Web.
Flag State Control. (2009). Flag State Control. Web.
Regulatory Framework. (2009). Regulatory Framework. Web.
Effective Flag State Control, (2009). Web.
Voluntary IMO scheme, (2008). Shipping Consultive committee. Web.
Barrister H. R., (2008). Weak international shipping registration laws: Need urgent reforms. Web.
International Transport Workers’ Federation, 2008. Flags of Convenience campaign. Web.
Young, E. (2005). Marauders continue to plunder the oceans. Web.
Manahanm D.T, (1990). Adaptations by invertebrate larvae for nutrient acquisition from seawater. American Zoologist, 30, 147-160.
Coles, R., (2002). Factors governing choice of flag. London: Lloyds of London Press.
Stpford, M., (1997). Maritime Economics. 2 th ed. London: Routledge.
The national Union of Seamen of Great Britan., (1981). Flags of Convenience.The unacceptable face of shipping, 1 – 15.
