Methods of Enquiry
There are various methods of enquiry used in various research and evaluation processes. Many methods of enquiry have been used for years in various quests by humans to unravel particular domains. Craig T. (2001) states that methods of enquiry are employed where people want to resolve more complex problems affecting them. Most of the methods of enquiry known have been used for years and constitute what has been termed the old-thinking methods of enquiry enlisting the analytic, deductive, inductive as well as consensual. The modern-think method of enquiry is known as the Systems thinking method of enquiry. The table below presents the methods of enquiry and their aspects entailing their limitations, key features, and merits of the methods of enquiry.
Methods of Enquiry
The Impact of Web 2.0 on society and Individuals
Contemporary societies have been transformed by the sweeping phenomenon of technological advancement and globalization among a host of others. The progress that has been registered especially in information technology has tremendously changed the way things are getting done nowadays. From a business perspective, the buzzword is e-commerce where businesses enhance their stratagem by manipulating the cyber landscape for various business thrusts enlisting marketing, networking, communication drives, etc. From a social world, Facebook is the place to be on the web in a plethora of social networking sites powered by the delights and merits of interactive web 2.0 programming languages which have transformed the web from a mere collection of static web pages to interactive interfaces soliciting user contribution. From an education perspective, the educational thrust has been tremendously impacted upon by the progress in Information technology. The developments in IT have seen the growth of what has been termed e-learning (Electronic Learning). The concept of online learning or e-learning entails the employ of the web and internet interfaces by various traditional and some exclusively online education entities to provide and conduct courses online. This has come with its merits and demerits.
The online degree facility of the City University of New York has been hailed for bringing about the aspect of flexibility for the students. The flexible nature of the online degree has opened up learning opportunities for working professionals who would otherwise not be able to handle work and attending classrooms or lecture rooms simultaneously. Online degrees come with a formidable aspect of flexibility and learning opportunities galore for anyone willing to upgrade themselves academically. Martin Ian (2001,)notes that although many have attempted to criticize the quality of the online degree in defense of the traditional degrees, online degrees is offered through a multifaceted and multi-dimensional cyber thrust which entails learning and interactive tools like wikis, and blogs which are user or student content web application used in various e-learning web interfaces. These; together with many other allow all the studentsare to be equal contributors of knowledge which is something that traditional learning models can not provide for instance; in a lecture room setting. Although some students will make contributions in class, not everyone does but through the wikis and blogs, students are required to make contributions and submit interactive threads or are prompted to give their views and perspectives on online academic forums, discussions boards, and other interactive interfaces. Martin Ian (2001) notes that the offering of the online degree together with the various interactive web tools used to support the learning process is in tandem with andragogical learning thrusts which have far outplayed pedagogical approaches of education in the critical aspects of student involvement and motivation. He underscores that in typical andragogical learning thrusts the learners are viewed and regards as equal contributors of knowledge whereas students are in traditional pedagogical education thrust students are large regards as mere recipients of knowledge. The former thus brings with it student motivational merits as learners feel that they are a significant part of the learning process whilst the latter would culminate in low morale for students and hence the ineffectiveness or failure of a learning process owing low learner morale. This has been the hailed vantage point of online degrees which are offered in procedures and processes that empower students to function in the learning process equally and stimulate their learning endeavors.
Online degrees place students in real information technology functionalities. This is achieved through the requirement for the students to conduct all course correspondence through online facilities over the internet. Students in online degrees also have to make the most of the technology to interact with other students, conduct researches, consult online libraries and use web tools like wikis and blogs as well as other utility applications such as excel or SSPS applications, etc to complete their academic tasks. Powers Wendy, (2006) notes that this is the most practical way of empowering students with knowledge and skills beyond the scope of their core degree curriculum. He notes the students who complete the online degrees are better prepared for the workplace context as they would have mastered critical aspects of information technology, skills which will be required in any workplace environment given the growing use of IT in modern society. What is notable in the foregoing is therefore the implication that students completing traditional degrees in conventional brick and mortar settings are less prepared for the real-time career environs as they may still have to go through the complex process of mastering various IT systems requisite for routine career tasks.
Although some arguments for the merits of online education have been advanced the learning model is not without its limitations though. In a survey conducted by researchers cited by Marcus Henning (2007) to establish the opinion of the employers on online degrees, more than 60 percent of the employers indicated that they perceive online degrees to be of lower quality than traditional degrees. Arguable as it may be, this has direct implications for the hiring decisions of the employers and it implies that traditional degree students will be first preference to employers than online degree students. One of the emerging concerns on the thrust of online degrees is the question as to whether online instructors will be able to own up to the challenges of meeting the future demands of online learners which are projected to increase. The other set back fore-learning is that the adoption and enhancement of online learning programs come with budgetary constraints for the development and sustenance of pedagogical competence of online instructors. Nonetheless the foregoing can not suffice as the sole basis for an argument against the merits of online degrees versus traditional degrees. With more research being conducted in the areas of improving online learning it can be expected that the future of e-learning will see more effective and efficient e-learning thrusts.
The Internet landscape has transformed tremendously from the bundle of static web pages of the web 1.0 eon to more dynamic and interactive web functionalities which characterize the web 2.0 eons. From a societal perspective, web 2.0 has brought tremendous changes in the firms to conduct their business. It initially sounded like a winning situation – absolute free money – for all internet access providers. By simply tracking their users’ personal surfing habits, they can effectively deliver ads to their target audience’s interests and claim a portion of the budding online advertising market heavily dominated by internet search companies yet these efforts to determine consumer interests through the internet continue to rise.
Marketers are in constant flux to develop new strategies and expand their markets and achieve advantages presented by economies of scale through globalization. Every supplier all around the world aims to effectively tap their target audience, to effectively inform them of the commodity being offered and make a sale, many methods have been employed and revolutionized and of this the newest being digital advertising. This method provides the opportunity to easily manipulate and work with the content in hand. An example of this may be that data sent to mobiles and the internet can be detected and traced easily. Online advertising has changed the realm of advertising in the past few decades by adding a lot more features t conventional brick and mortar advertising could only imagine. Chief Executive Officer of the interactive advertising bureau (IAB) Mr. Rothenberg that the field of interactive marketing has been steadily growing and developed vitality and more areas of expansion are expected wince consumers in this age are spending double the time online compared to the past. (Potter, 367, 2005)
The Internet has recently gained a lot of popularity in third-world countries. In countries like Qatar when the research was carried out it was found that internet usage had grown by over sixteen percent. The majority of which contained digital subscriber’s line, internet accounts have risen from fifty thousand to about eighty thousand. With the growth of internet-based businesses like Armex international limited. A courier provider who opens clients’ mailboxes in UK and USA for their online shipping accounts. Today internet advertisements can track down users with the use of cookies and other complicated algorithms to provide accurate information to the end-user. In this way companies can efficiently spend their marketing budgets; by targeting only those potential users. This is made realizable by using the various media options i.e. cost per mile or cost per click of mouse and cost per acquisition. An example may be a company as per wish may buy advertising space but only to be shown on an oil and gas website and only when a certain individual is accessing the particular pages to maximize revenue to achieve these certain results, behavioral approaches targeting the advertisements for internets are used. Companies like Phorm or NebuAd are said to have developed new software that is pre-installed on networks of internet service providers which usually intercept web pages requests generated by the users and they surf the internet. These pages in question are delivered as per request but are scanned for certain keywords to build a general profile of the user’s interest. These profiles are then used in targeting consumers more effectively. The future still presents to be a little is expected to get more technologically sophisticated as seen in movies like the minority report where the actor Tom Cruise passes by a billboard and the billboard recognizes him and says “Hello Tom.” (Potter, 367, 2005)
IT Business Strategy case scenario
IT Business Strategy has come in the contemporary business development milieu to enhance effectiveness, efficiency, and competitiveness. As such, regardless of the size or operation capacity of a business entity, enterprises need to implement IT project plans in tandem with their growth and diversification as well as long-term sustainability strategies. Computers will enable the Apex salon business to streamline operations and enhance efficiency. The time saved by effective working systems will enable personnel to focus on other aspects of the business maintenance or fielding phone calls. The proposed Information Technology design will enable them to have tabs on their entire salon branches across the entire market area covered (national). IT models will come in place of the client cards system as well as the paper and pencil inventory. The system will enhance Apex’s marketing stratagem as it will facilitate the taping of the merits of direct and relationship marketing by rolling out mailing lists, generate customer profiling, and any forms of reports needed.
An intact and feasible IT design is needed for Apex to cater for the following aspects:
- Customer management (Profiling, Purchase history, contact detail. etc)
- Payroll procedure for the entire national framework
- Inventory
- Cash Flow (accounting methods)
- Credit Card transactions
- Customer Feedback (Customer satisfaction)
- Employees’ appraisal
The IT project company commissioned by Apex has developed its IT system in the mold is the Soft Systems Methodology (SSM). SSM is an organizational thrust that focuses on organizational process modeling. The method can be applied for the solution of a general problem and is much handy and often used in various change management approaches. The approach to accomplishment of goals of growth, sustainability, and most importantly, competitiveness by the IT Project Company can be tallied with some stage components of the 7-stage SSM model.
Enter situation considered problematical (SSM Model Stage 1)
The situation considered problematic in line with conceptual frameworks of the SSM model was characterized by the rapid growth of Apex which saw the expansion of the business of the company into over 24 countries (to date) across the region. The problem specifics into this entail the need to formulae feasible means and operational models that would suffice for optimum efficiency and service delivery in all the business network areas. Apex also faced stern competition from other companies which were also offering similar products and services within the same market targets. The other dynamic enlists the need to keep pace with modern and contemporary ways of conducting parcel service delivery service. This is perceivably in the premise that technological advancement is aimed at enhancing efficiencies and simplifying the way things are done. This has necessitated the formulation of a dynamic IT model for Apex.
The development of the model has also followed the progression outlined in the SMM model which enlists the following stages:
- Outline the problem scenario
- Generate root definitions of working systems of purposeful activity
- Assemble conceptual designs of the systems outlined in the root definitions
- Comparing designs with actual-world situations
- Define possible alterations which must be both possible and feasible
- Take action to improve the problem situation
One of the declared goals of Apexin the recent dispensations is that of the company’s endeavor to be a leader in e-business and salon service and product provision. Owing to that, Apexhas intensified its thrust in tapping the merits of technological advancements to enhance its operations, cut costs and enable customers to manage their purchases and accounts with Apex.
Among other things the facility offers the customers the following:
- Send and follow orders all at one point
- Cancel orders and keep purchase records.
- Store tracing numbers and addresses online.
- Generate and print Apexlabels from the internet
- Pay for costs through a credit card, or transfer chargers into an Apex shipping account.
- Access stored purchase and transaction details for up to 3 months
- Set and store preferences like origin address, payment type, etc.
- Register for notifications via e-mail, wireless phone, or PDA
Data obtained from the published company literature on Apexoperations designs indicated that the company needs to cash in on the aspect of providing Information clients need.
The customers have the ability and advantage of managing their dealings with Apex well ahead of time. Needless to say, such service rendering which is indisputably pro-customer satisfaction than operations inclined has tremendous results in form of customer retention. Customer retention is indispensable to any strategies of long-term growth and sustainability. The growth rates of the company in the past can be as well attributed to this fact although growth can not be explored in a single dimension. The company may be expected to record related and proportional growth rates into the future holding other things equal and assuming that the company will maintain its policies and organizational models which have catapulted its growth levels to where they are currently.
An outline with Apex Managing Director Feltham has implied that the company will continue on the same pathway which has resulted in sustained growth and sustainability in the past years. She outlines, “If I were the company’s marketing manager and IT manager I would continue to devise new ways of selling our products and providing our customers with more information, the internet must provide us with an instant means of communication with our customers and allow them to track their products virtually anywhere at any time, I do not believe we have seen the last of what the internet and other new technology has to offer Apex and our customers. It will be the Apexmarketing department’s job to tell the world about the merits of our services and continue to create and reinforce our prized corporate image.”
(Dessler 2008) concurs with the foregoing, “Enterprises must make smooth transitions to the future. Many goals were set for the new millennium. One goal set by the development department was to identify and apply new technology that would improve existing operations and develop new business.”
According to Dessler Apexhas succeeded because of the drastic communication advances. He further illumines that the customer is ultimately satisfied with the reliability of companies to deliver on time. This is the marketing factor that sets Apexa a step above the competition. All decisions were made in the respect that the company would continue to bring the customer more than they expected. In turn Apexis a well profitable enterprise. “The environment provided by companies keeps customers, employees, and managers working hard to keep up the high standards set by today’s customers.”
Apex faces the challenge of upping its technological capabilities to run in tandem with technological advances. One Apexcompany representative asserts, “Low costs are another reason that their customers keep coming back. The growth strategy chosen by management is working. It is designed to take advantage of their competitive strengths while maintaining the focus on meeting or exceeding customer requirements… Upper management is impressed with the progress.” This must be enhanced by putting together of a variety of online services that assist customers to trace their purchased packages easily. The company budget for the IT strategy testifies to Apex’s decisiveness on the endeavors to tap technological merits and capacities to enhance efficiency, competence, competitiveness, and more importantly, sustainability.
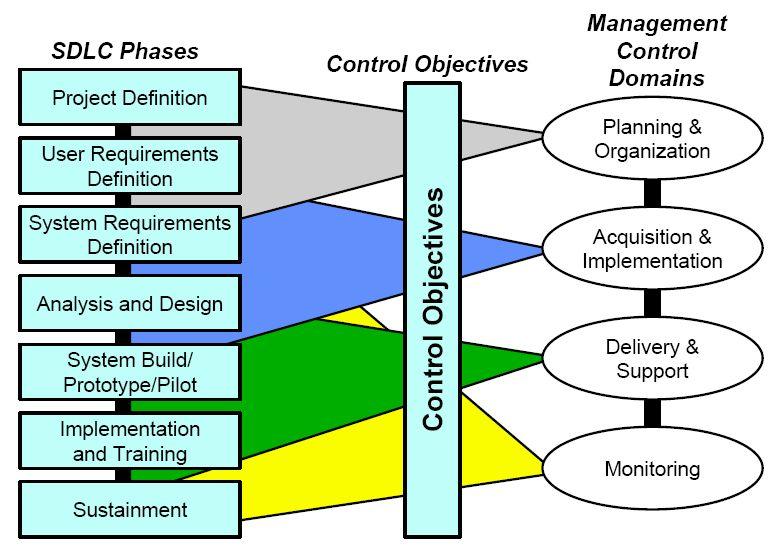
The Apex model is also in tandem with the Systems Development Life Cycle (SDLC):
E-government and ethics
Moral choice is deemed to be crucial for honorable administrators. It normally consists of three equally important criterions such as being:
- disciplined people,
- active participants in their organizations,
- independent judges.
Given the benefits incurred to both individuals and organizations, administrators in every single organization should employ—besides technical skills—“moral choice” to effectually lead the organization of the society, as well as resolve any problem in scenarios related to the implementation of information systems.
organizations particularly in public administration are bound to lead people in morally acceptable ways by charting and adhering to ethical manners of getting core goals and objectives accomplished. Such organizations have to place their key policy and ideology on the succor of values and morals governing normal human conduct and behavior. Values in this conceptual precinct are perceived as those ideas regarded as worthy, estimable, and important. By extension, values can be viewed as those concepts that govern human behaviors like freedom, equality, education, etc. Ethics are thus held as objective since these set the basis for a pattern of universality in the manner in which human conduct can be classified as either ethical or unethical, moral or immoral.
Talking about public administration responsibility and ethical administration, Spaemann, R. (1989, p. 63) dwells extensively on how the regard for ethics and morals must come together in the public admin. He reinforces the aspects of the thinking “ethically”. More importantly, the scholar underscores the aspect of responsibility on the part of public organizations and administrations. The author takes a deeper thrust stating certain ethical letups in the contexts of justice frameworks in a manner leading to a more serious categorization of certain organizational decisions and operations as just or unjust, ethical or unethical. Various reasons can be cited to substantiate this line of argument. Spaemann R. (2003, p. 11) states that public canvassing and lobbying for the implementation of the national ID program. He states that the UK government for instance has overemphasized the reasons for more security measures to be sustained through the ID system while downplaying the security and privacy violations of the civil rights which come with the model and implementation of the national ID system.
On the aspect of public information and education, there has been noted that the government is backtracking in informing the public how they seek to strike the balance between accomplishing the envisaged security goals through the ID system and regard for civil liberties and the right to privacy. Inadequate information results in misinformation through the withholding of crucial information especially around the functionalities of the National Database and other critical aspects of the ID system. Misinformation is tantamount to a violation of the public’s basic human rights. The active exponents of the national ID system have stated that the government security services organs face an ethical obligation to give authentic information to the recipients who have the right to accurate information for their welfare with regards to implications of the entirety of the National ID system.
Spaemann, R. (2003, Op.Cit) states that the essence of the state constitutes the setting up of institutions endowed with the power to formulate rules that set the framework in which the society can be governed in an envisaged harmonious manner. The concept of governing in its own right is a means by which the state shapes the society. There is a piece of overwhelming evidence to substantiate the notion that society does influence the state. This has been based on the underlying understanding that the governing institutions that constitute the state are formulated and framed within the culture precincts and various value systems of the society within which they function. “The premise of a people’s culture enables the evaluation of certain government and governance decisions and actions leading to the classification of the government’s moves as either ethical or unethical”. (Spaemann, R. 2003, Op. Cit)
Cultural Universalism holds that cultures originate in one point and thus are, and must be mutually compatible. The concept embraces the notion that there is one ideal model of human rights and a global way of doing things (Culture). Universalism flies at the core of contemporary human rights statutes. Arguing as an exponent of the launch pad of the foregoing Bob Russell (2008, p. 13) argues that the British must not be bullied to accept the national ID system on the simplistic basis that the system has been approved and used in other countries. He asserts from a cultural relativist perspective that the Britons hold the national ID system as unethical basing on their value systems, then the government must consider the public opinion and respect their will and shelve the national ID system.
Universalism holds in its score that there is a foundation human union which regards all individuals are entitled to basic rights regardless of their race, origins and religious beliefs, or otherwise. From another perspective, cultural Relativists hold that cultures are intrinsically dissonant; that the cultures of the world can not be thought to be compatible neither can they be blended. From the foregoing perspective, it can be noted how especially mature democratic states are shaped by the global society in the premise of human rights and also how the states formulate governing concepts based on the Human Rights Charter framework. Notably, the concepts also influence the conduct of the society, and hence the flow of influence is mutual between the state and the social paradigms.
In states that are categorized as cultural relativist, governing principles are formulated from the premise of ‘national’ culture with no particular regard for what global culture entails or stipulates. The dilemma in culture melting like the UK is that there is no single national culture as the UK society is made up of various culturally diverse nationalities with diverse value systems. Bob Russell (2008, p. 7) observes that although there is no cultural unison in the UK society there is a profound public chorus on the disdain of the proposed national ID system. The scholar notes that regardless of the tenets of the relativist cultural thrust; no state is immune to global influence in the wake of contemporary sweeping phenomena such as globalization and aspects like acculturation and cultural pluralism. “The UK populace will at have to face the reality that the world is under the irresistible influence and impact of the global approach to contemporary global problems such as climate change and terrorism, as such, Britain will adopt measures similar to those adopted by other states and the populace must accept that”. (James, Neil. 2003, p. 54).
He asserts that the core of public governance policy must recognize the rights of the populace. The previously cited scholar defines policy as a deliberate or purposed blueprint of action to govern decisions towards the achievement of reasonable (rational) outcomes. The import of the term makes it squarely applicable to the UK government as well other associative governing institutions. Policy differs from rules and law. Rules and laws constitute the legislature and the judiciary aspect of government yet policy focuses on guiding the decisions making processes such that all variables and the decisions set are modeled to facilitate feasible decision-making towards the kind of actions perceived to precipitate the best of outcomes. In light of the foregoing, it is apparent that the UK government has missed the mark in making and implementing ethical decisions at least in the light of the views of the majority of the Britons.
In the quest of the UK Home Office to transform into e-government models with the intensive employ of IT for the stated civil securities, the implementation of IT models and measures must thus draw cues and run in tandem with the host of ethical decision making and implementation frameworks and theories to ensure the accomplishment of set goals acceptably. Policy or policy study may also be understood as the process entailing the making of critical institutional decisions including the establishment of different alternatives like program or expenditure priorities. According to the idea, the identification and selection of the best alternatives are largely shaped by the perceived impact that the selected and other alternatives may have. Francis Elliot (2008) further outlines that policy can also be interpreted as “…political, social, managerial, fiscal and administrative, etc”
Security and ethical measures
The government IT departments frequently suffer from various malware on the institutions’ computer systems. Companies and government institutions and end-user providing and making use of the critical database service and products such as the UK Home office have to follow provided and available guidelines to avoid data loss and the compromise of the people’s private data. Technology analyst and Information security consultancy firm Gartner provides seven security issues that must be discussed and clarified by and with the government representatives to assure the populace and stakeholders of the feasibility of the national ID systems.
The Firm Gartner presents the following issues that must be clarified:
- Privileged user access-On this aspects users’ access status must be clarified to establish who has special access to data as well as enquire about the hiring as well as the management of such security administrators
- Regulatory compliance-In the second aspect users will establish if the Home Office Data Security organ will be open to external audits and or security certifications.
- Data location– On the third dimension of data location the data security firm advises project developers to verify if the organization provider allows for any control over the location and storage of data
- Data Segregation– On this aspect, the project developers need to clarify if encryption is available through all service levels as well as whether the encryption schemes were modeled and tested by experienced experts.
- Recovery-On the recovery dynamic the proposed development must outline as well as establish what may happen to the sensitive data should disaster strike, on this dynamic as well as ascertain if in cases of disaster there are data restoration systems in place and also establish how the data restoration process is expected to take place.
- Investigative Support– On the investigative support aspect there must be detailing on user ability and privilege to detect any suspected or inappropriate or illegal activity.
- Long Term viability– On the last dimension which regards long-term viability there must be established what is likely to happen to data in the long run as well as how the data will be restored as well as the format it will be restored in.
References
Bacheldor, Beth (2008), Security IT, A Comprehensive Guide, 3rd edition. New York: Wiley.
Barker, E. (2007), Mapping the Iceberg. NALL Networking, Ohio, US
Bob R. (2008), Structured Naming Designer for the Internet; Patent for the internet, Portland, OR, USA,
Codd, E.F. (1970), IT Learning: Professionalism, Regulation matters and Performance, San Francisco: Pfeiffer.
Christopher, H. (2008), The Service-Driven Service Company. Harvard Business Review, NYK.
Craig T. (2001), Security Engineering, New York: Wiley, USA.
David, C. (2005), Connecting Security as well as Multi- Homing in a HIP Pathway, Delivered at Interconnected and Dispersed configurations Security Convention San Diego, CA, USA..
Edward, H. (2007), IT Implementation in Context,Rout ledge, USA.
Francis, E. (2008), Data Security and Ethics.New York: Harper & Row
James, (2003), The World Crisis in IT, A View from the Eighties, New York: Oxford University Press.
Kablenet F (2008), Data Security and Human Rights, McGraw Hill, ASA.
Lord, C. (2008), System Pointers, Delivered at University of Princeton.
Lords, H. (2005), International Journal of IT Development Leeds University Business School, The University of Leeds, Leeds, UK
Lynne, F. (2006), Naming and Binding of interconnection destinations, MIT Lab for Computer Science. Oak Press.
Lightstone S. & David G. (2007), Host Identity Indirection Configuration (HB) Swedish National Computer System.
Martin Ian, 2001, Youth Education, Routledge and Falmer, London and New York.
Paul B. D. (2008) European Business Management School, University of Wales Swansea, Singleton Park, Swansea, UK, [email protected].
Rubin, E. & Babbie F. (2001), Internet Security, How Formal IT Education Can Help. Baltimore, Sidney.
Shafiroff, M Jason, M (1990), Information Age and Ethics, Mews Publishers, WV, USA.
Spaemann, R. (2003) Design for Introducing Disruptive technology into the inter-connection, Millen Press, Sidney. AUS.
Whitman, M. and Herbert M. (2009), Principles of Information Secuirty, Canada: Thomson Publishing, Canada.
Whitman, M. & Mattord, F. (2009), Workplace Learning, Prentice Hall International Ltd, London
